In first and second part we managed to somehow bring up our Two-Tier PKI infrastructure on Windows Server 2022. In part three, we will configure root and subordinate certificates deploy via group policy.
Root certificate from RootCA (test-rootca_TEST-ROOTCA-CA.crt) should be in C:\CertData (I also copied it to C:\Windows\System32\certsrv\CertEnroll folder). Subordinate CA from CA1 should be in C:\Windows\System32\certsrv\CertEnroll folder (TEST-CA1.test.local_TEST-CA1-CA.crt).
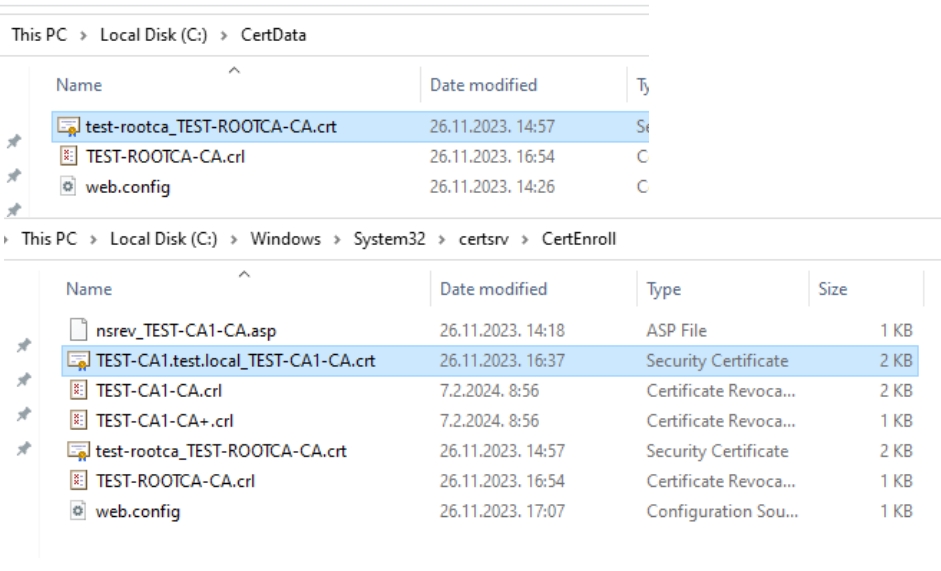
We will now create new folder named C:\Certs on CA1 server and copy test-rootca_TEST-ROOTCA-CA.crt and TEST-CA1.test.local_TEST-CA1-CA.crt to that folder.
We will rename test-rootca_TEST-ROOTCA-CA.crt to RootCA.crt and TEST-CA1.test.local_TEST-CA1-CA.crt to CA1.crt for easier understanding.
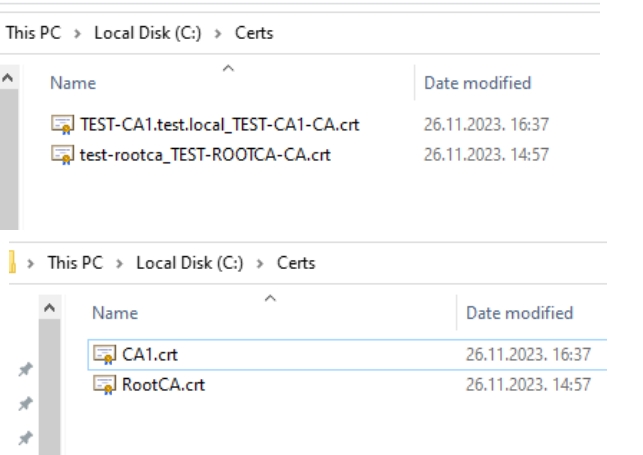
Now copy contents of C:\Certs directory from CA1 to domain controller DC1. Create C:\Certs folder on DC1 and copy contents of C:\Certs from CA1 server.
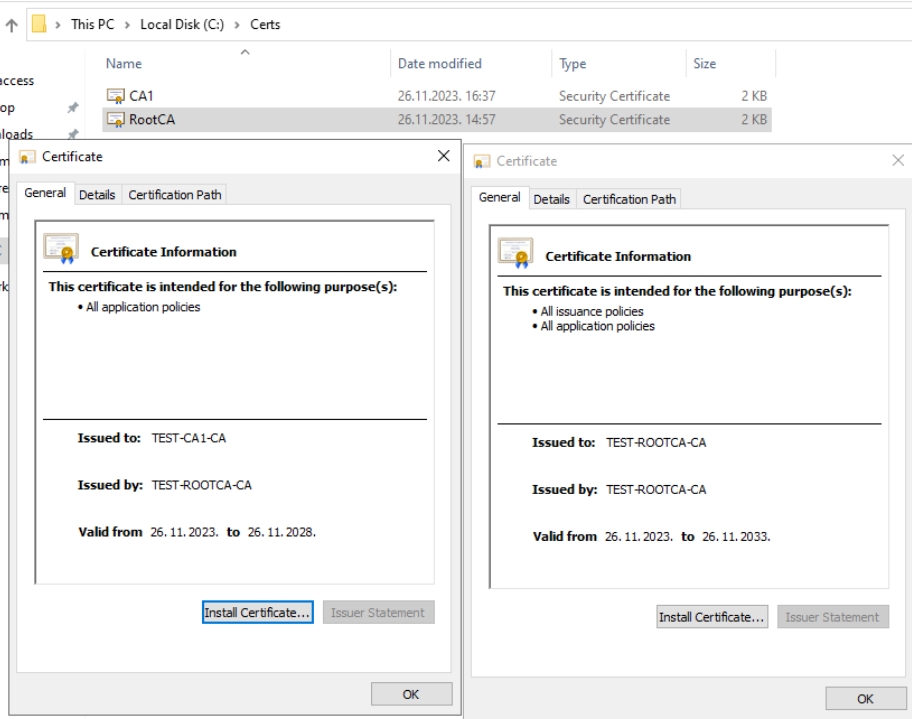
On DC1 in C:\Certs folder if we double click on both certs, they should open, and we will verify that those are certificates from RootCA and CA1 – RootCA is valid until 2033 (10 years) and CA1 is valid until 2028 (5 years)
If you have multiple DCs in your domain, this directory should be created on each of them and these certs should be deployed to them.
On a DC1 in Active Directory Users and Computers I usually create two new OUs – Servers and DomainPCs. We will need them in this guide, since we will create group policy on them. And group policy will apply to them with the certs mentioned above.
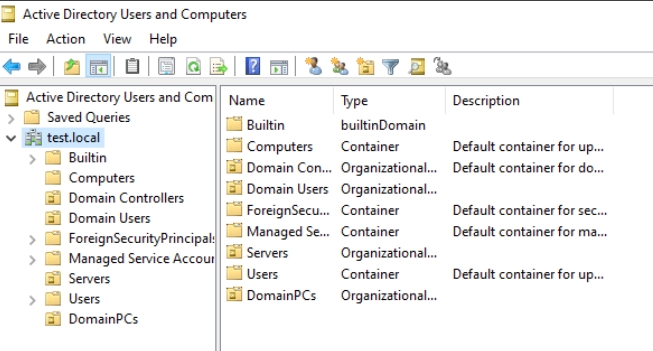
In this guide, you will need to add DomainPCs OU to Active Directory Users and Computers. I also installed one Windows 11 VM, named Test-Client1 which I added to domain, and after that moved Client1 from Computers OU to DomainPCs OU. This is so that we can test if the Client1 will apply group policy we will create.
Deploy RootCA and Subordinate CA certs via Group Policy to Domain PCs
You also can use steps below on the OUs you have created.
On DC1 in search type in gpmc.msc and that will open Group Policy Management. Find DomainPCs OU, right click on it and select Create a GPO in this domain, and Link it here…
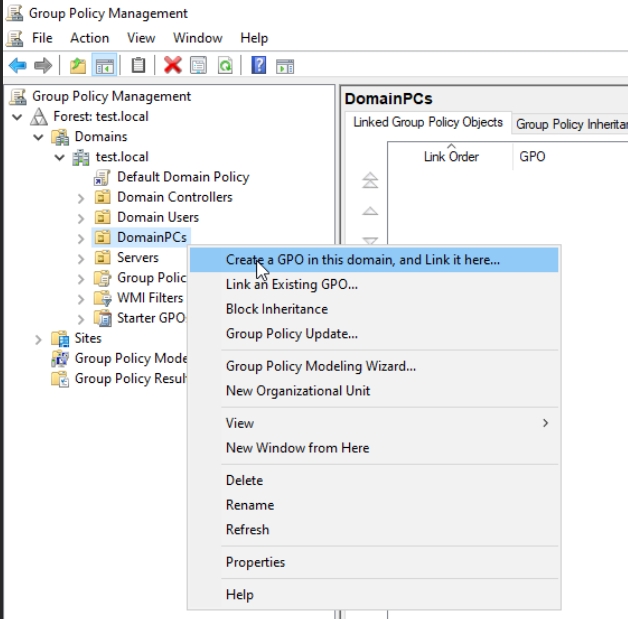
I do not recommend modifying Default Domain Policy, to be fair, in my whole career, I never added anything to it. It is good practice to add policies to the OU that you need them on, and to create new policy for every setting you make.
Nwe window will open, in Name field I entered PKICerts1, I left none on Source Starter GPO, and pressed OK.
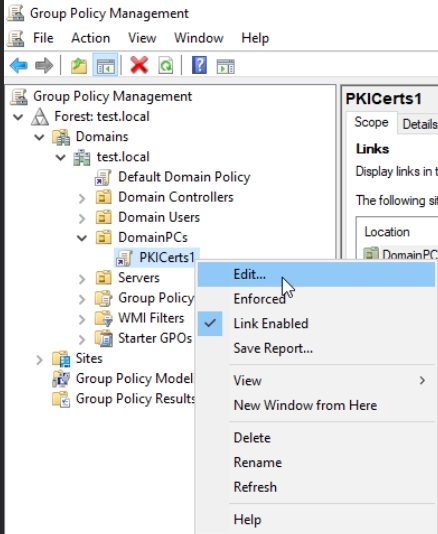
Expand DomainPCs OU and right click on PKICerts1 and select Edit
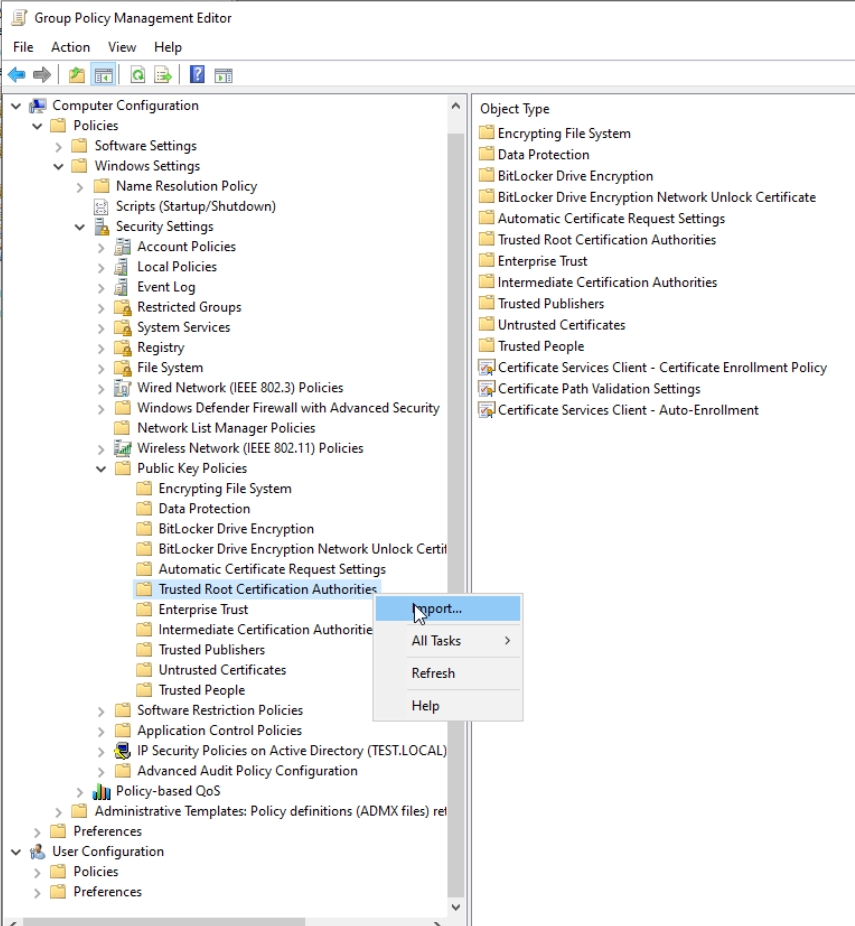
Group Policy Management Editor will open – expand following – Computer Configuration | Windows Settings | Security Settings | Public Key Policies | Right click on Trusted Root Certification Authorities and click on Import…
In Certificate Import Wizard, Browse to C:\Certs and select RootCA.crt file,
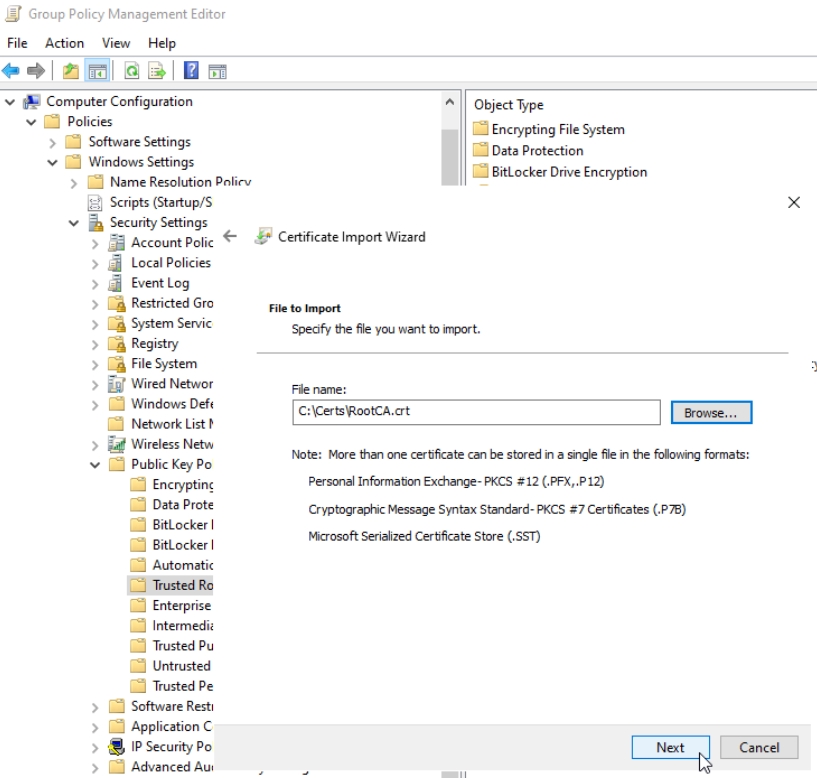
Make sure Trusted Root Certification Authorities is selected, press Next and then Finish.
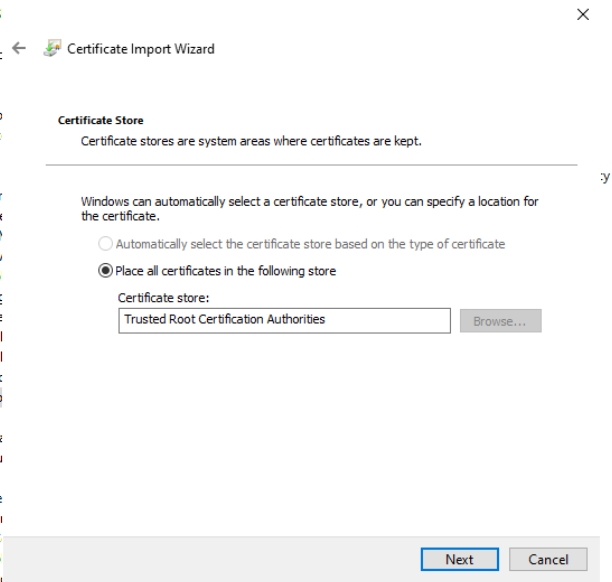
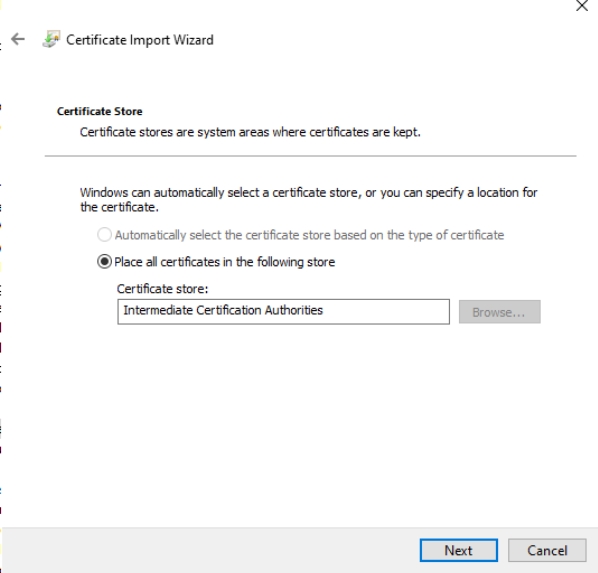
Stay where you are in GP Management Editor, and right click on Intermediate Certification Authorities and select Import
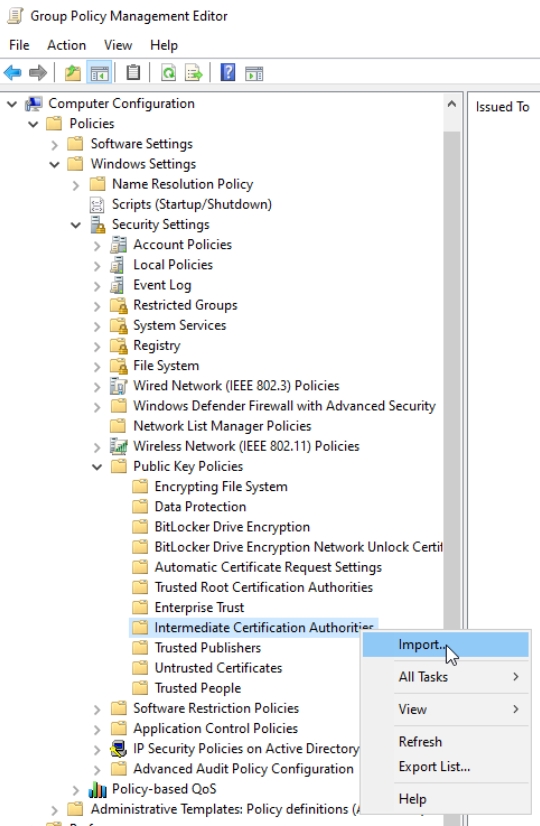
This time select CA1.crt and press Next
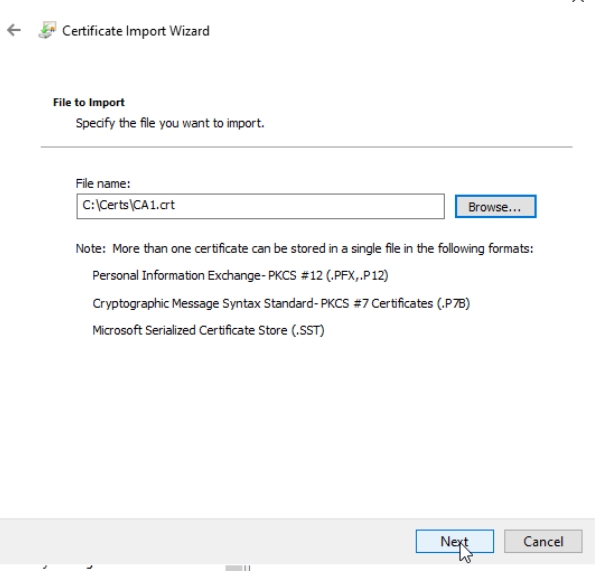
Make sure that Intermediate Certification Authorities is selected, press Next and then Finish.
Import will be confirmed as success.
Now, we can close Group Policy Management Editor.
Let’s now quickly check on Test-Client1 PC if the certificates are visible.
On CLient1 VM, start CMD as admin and type in following
gpupdate.exe /force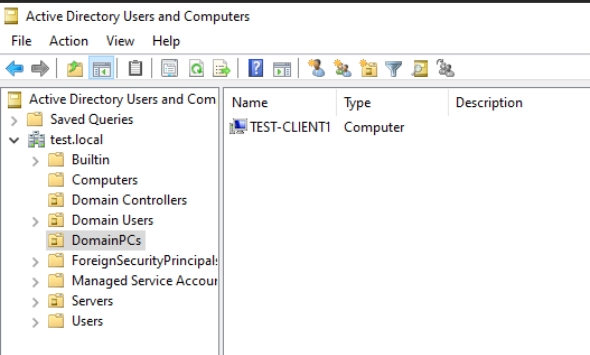
On Client1 VM, open MMC, and add in Local Computer Certificates. If we go to Trusted Root Certification Authorities – our RootCA should be there. Same goes for Intermediate Certification Authorities.
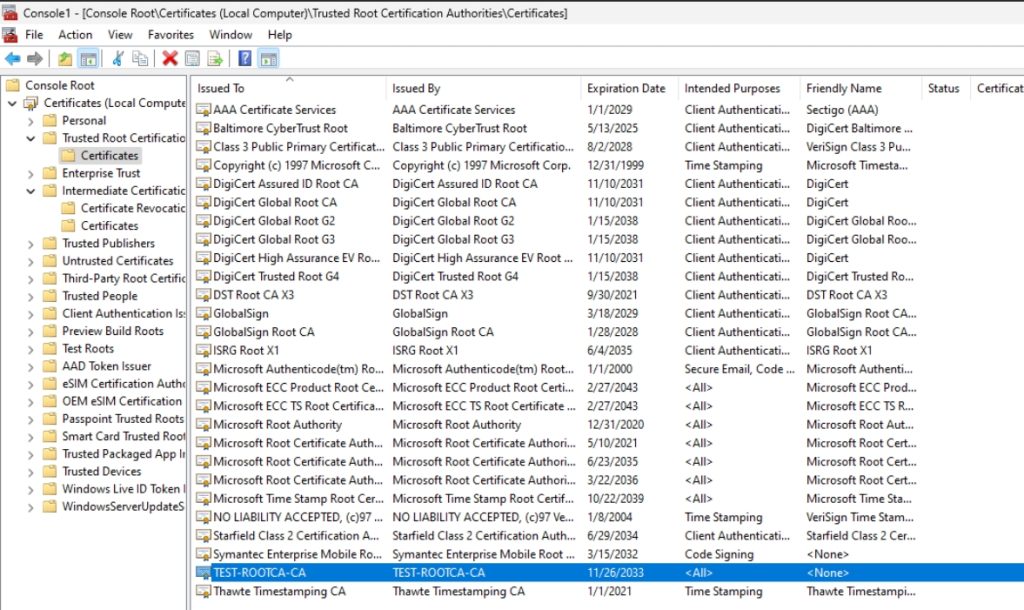
It is also possible that you could see duplicated certificates, that is completely normal phenomenon.
There is one more thing we must do, and one more thing you may or may not need.
Deploy the Root Certificate to the Domain Controller
We can do this two ways – one is to link PKICerts1 policy we created to Domain Controllers OU – we won’t do that here, we will use second method, and that is to manually install RootCA.crt and CA1.crt
Open C:\Certs on DC1 and double click on RootCA.crt and select Install Certificate…
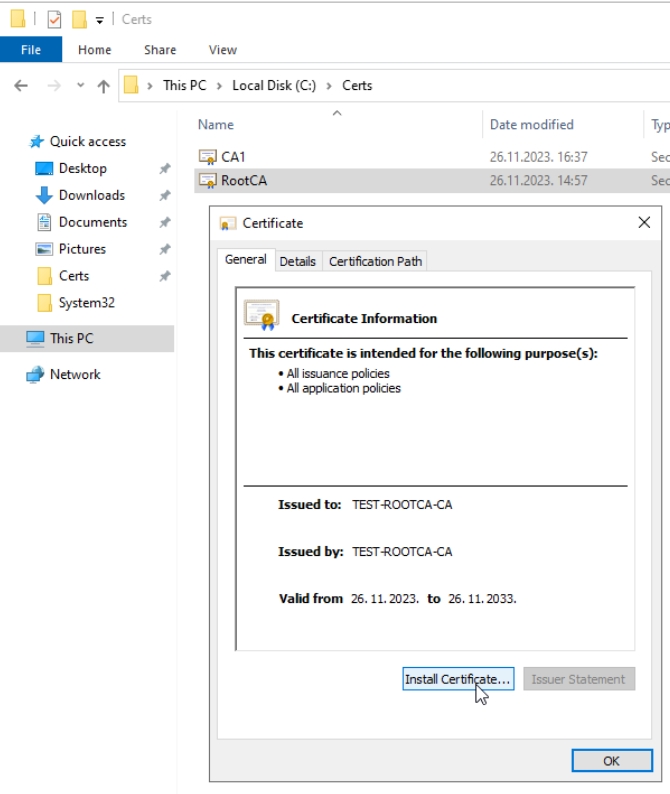
Select Local Machine
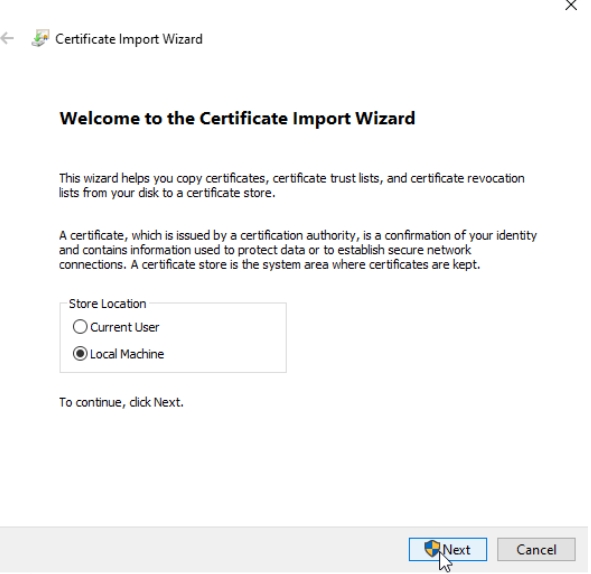
Select “Place all certificates in the following store:” and select Trusted Root Certification Authorities – Next and Finish
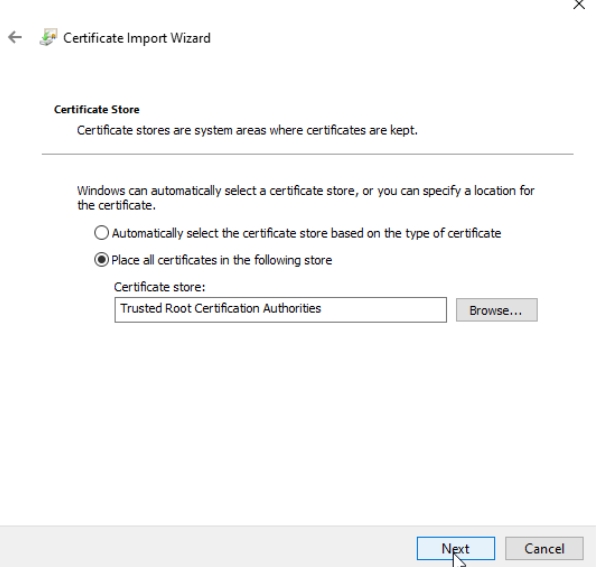
Now we are done with part that we have to do.
Optional – enable access to certs for Linux, Android and iOS machines
This step is optional, but if you have Linux in your environment, or use Android or iOS devices, this will come in very handy.
We will do this part on CA1 server, which already has everything in place, and has certs in C:\Certs folder. We now only need to create a new virtual directory in IIS.
Now, on CA1 server, start IIS Manager / right click on Default Web Site and select Add Virtual Directory
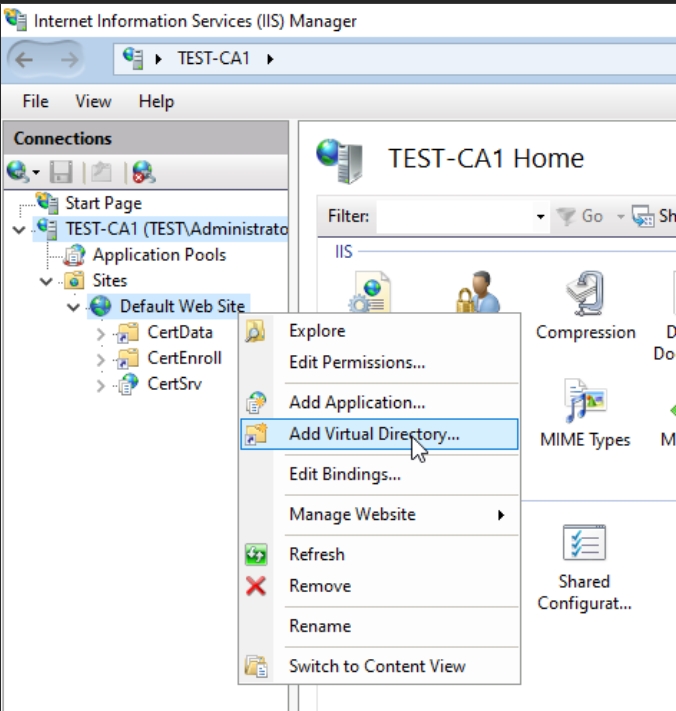
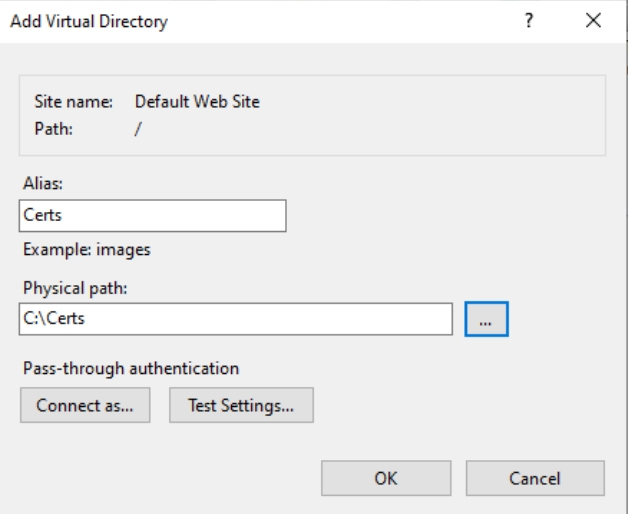
I created alias Certs and pointed to C:\Certs dir as physical path.
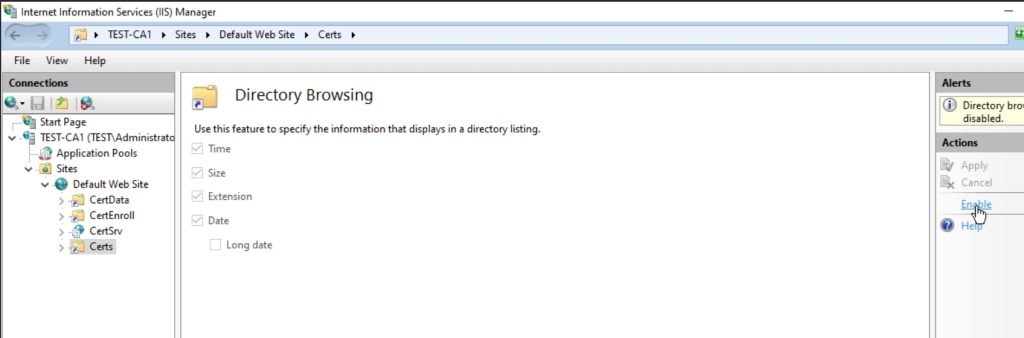
Click on Certs directory under Defautl Web Site, select Directory Browsing, and in Directory Browsing click on Enable. Restart IIS for a good measure.
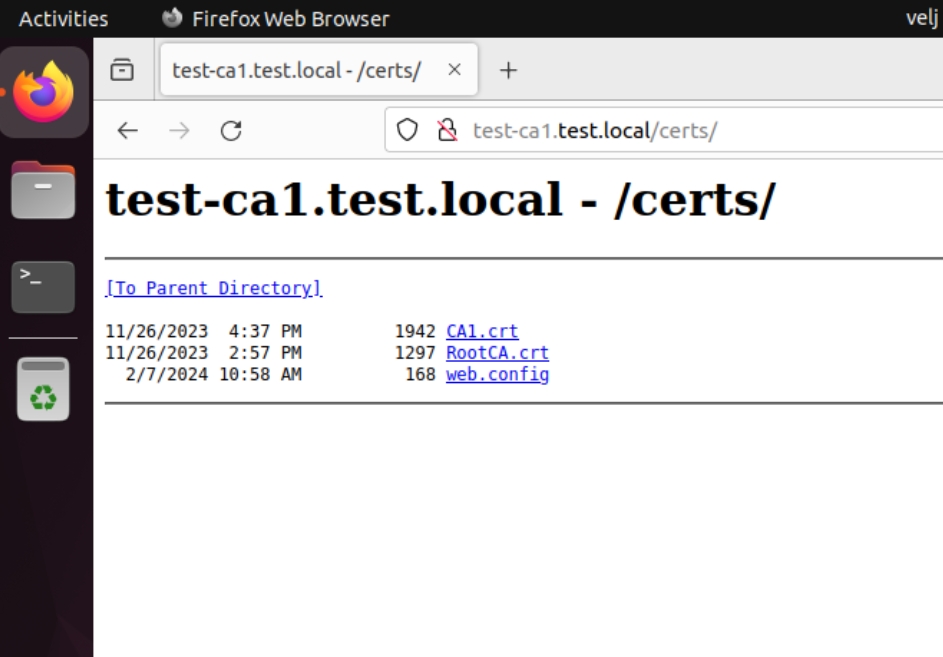
Now, if I go to the Linux client I installed in the meantime, and added it to domain. Here you can read how. If I enter http://test-ca1.test.loca/certs I will get folder with certificates that I need. Very useful.
That is that, we now have streamlined deployment of RootCA and CA1 certs throughout domain and different platforms, it will make our life easier and infrastructure more resilient.
Implementing Two-Tier PKI on Windows Server 2022 – Part 1
Implementing Two-Tier PKI on Windows Server 2022 – Part 2
Implementing Two-Tier PKI on Windows Server 2022 – Part 3 – you are here
Implementing Two-Tier PKI on Windows Server 2022 – Part 4
Implementing Two-Tier PKI on Windows Server 2022 – Part 5
Implementing Two-Tier PKI on Windows Server 2022 – Part 6
Implementing Two-Tier PKI on Windows Server 2022 – Part 7