In first and second part we were deploying PKI, in third part we were making available these certs on our domain via group policy, and now we will do Online Responder Role configuration – revocation of the certificates is extremely important role, and we will see how to do it properly now, in this guide.
We will do this on CA1 server. For a start we need to Add Online Responder role to this server.
I assume you know how to navigate Server Manager and how to add a role, so I won’t screenshot this step by step. Server Manager | Manage | Add Roles and Features | under Server Roles expand Active Directory Certificate Services and Select Online Responder – confirm additional pop-ups and finish.
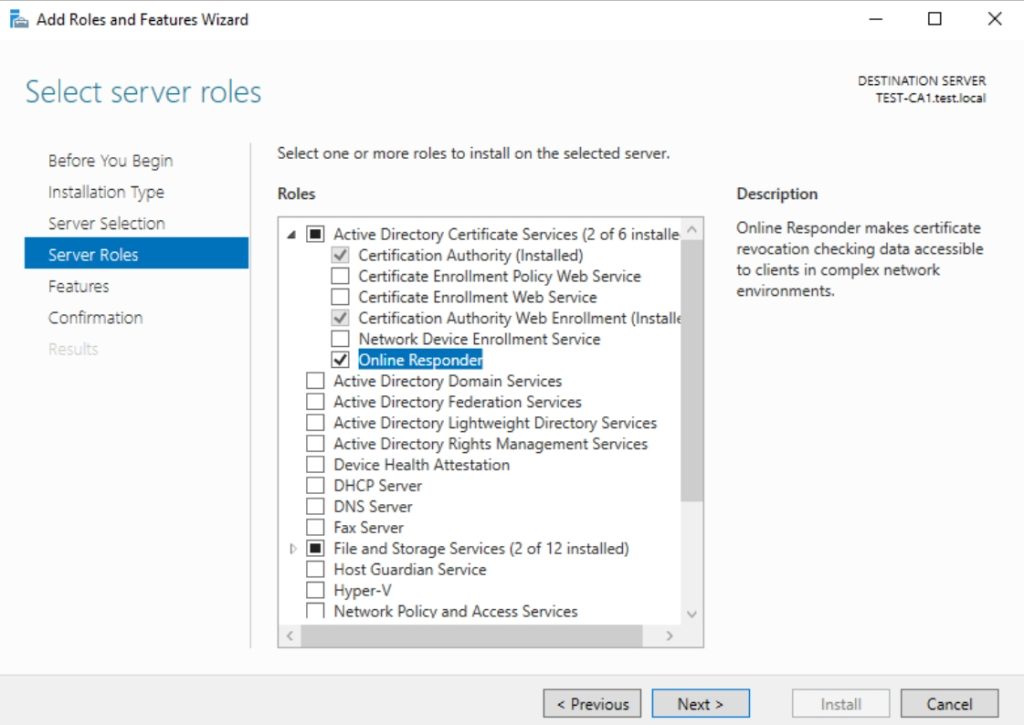
Enable Online Responder Role
Now, in Server Manager you will have under Notifications Configure Active Directory Certificate Services on the destination server and you can click on it to start configuration. I will just execute it through Powershell, but if you plan to go through GUI, You need to enter Domain Admin credentials on first screen, on second select Online Responder role and then confirm and close if you wish to go through GUI part.
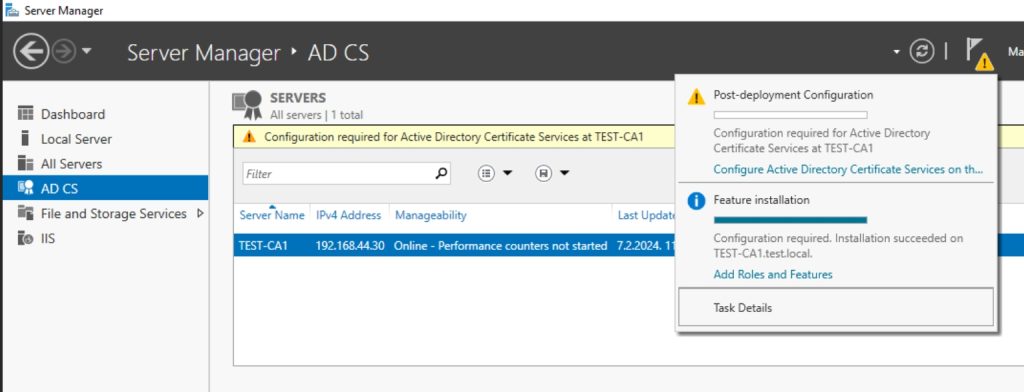
I will start Powershell as admin and type in following
Install-AdcsOnlineResponder -ForceIt will throw blank error field, without confirmation, but that is it, Online Responder Role is enabled
We will now validate OCSP role in IIS
!!! If OCSP folder is not visible, you can run following command in elevated Powershell
certutil.exe -vocsprootAnd then reset IIS
iisreset.exeAdd OCSP URL to CA1 (Subordinate CA)
We will continue our setup on CA1 server, and in search enter certsrv.msc and start Certificate Authority console. Right click on you Certificate Authority server (in my case Test-CA1-CA) and select Properties. Navigate to Extensions tab and select Authority Information Access under Extensions. Click on Add
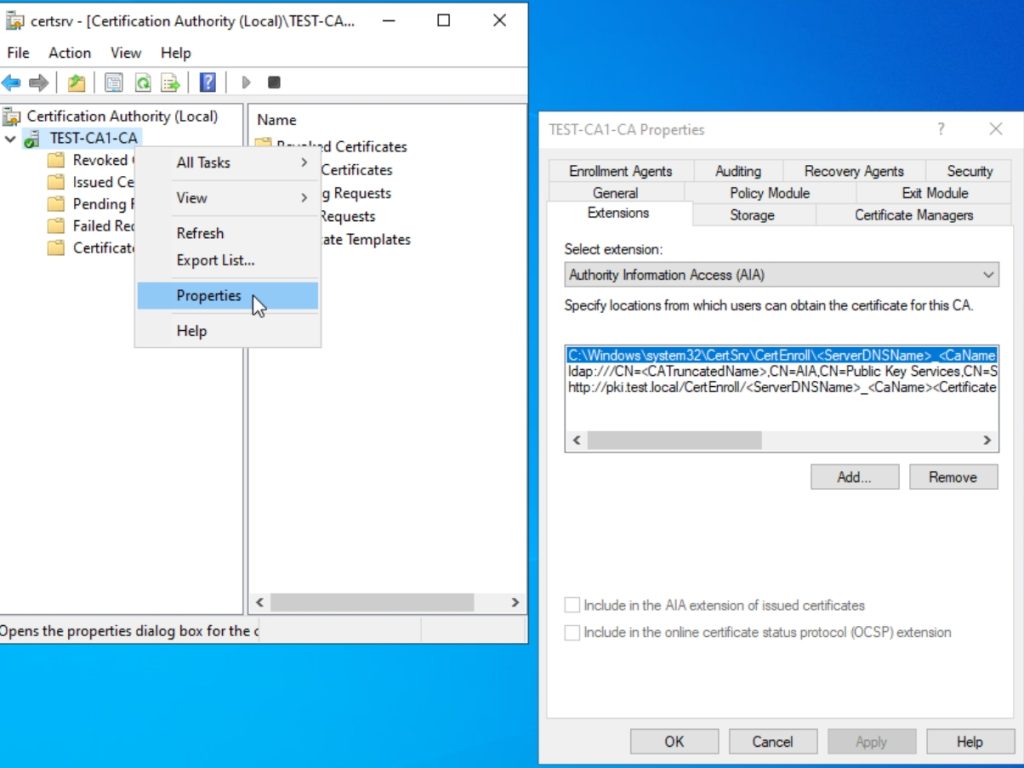
Under location enter http://ocsp.test.local/ocsp and press OK.
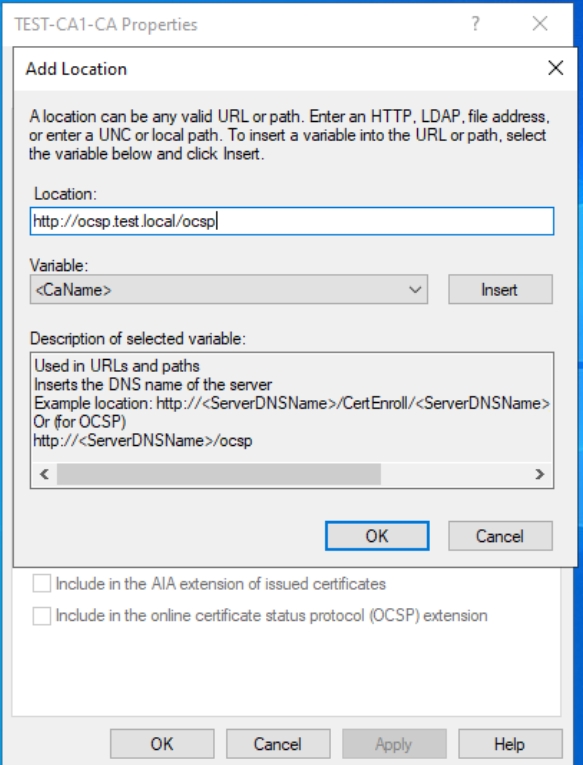
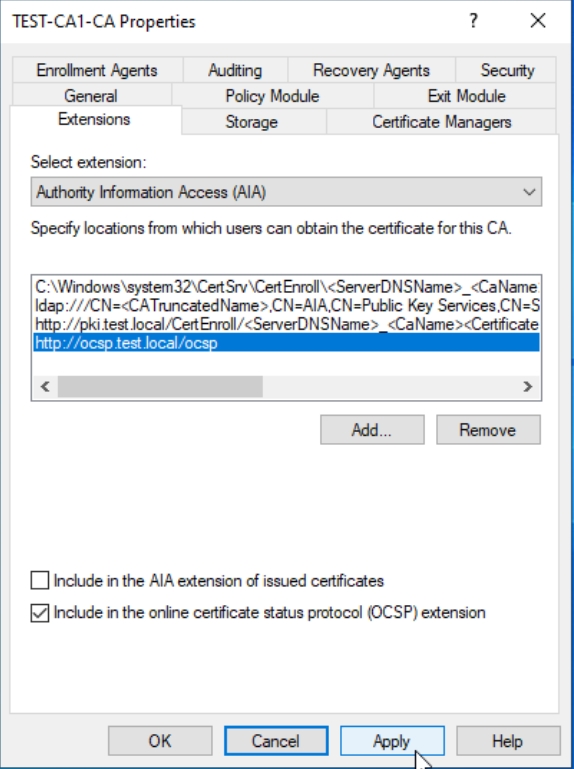
Now, select entered http://ocsp.test.local and make sure that “Include in the online certificate status protocol (OCSP) extension is selected. Confirm with Apply – OK – You will need to restart AD Certification Services – Press Yes.
Configure and publish the OCSP Response Sign Cert
On CA1 open Certificate Authority console (certsrv.msc). Expand your server and Right click on Certificate Templates and select Manage
Find and right click on OCSP Response Signing and select Duplicate Template
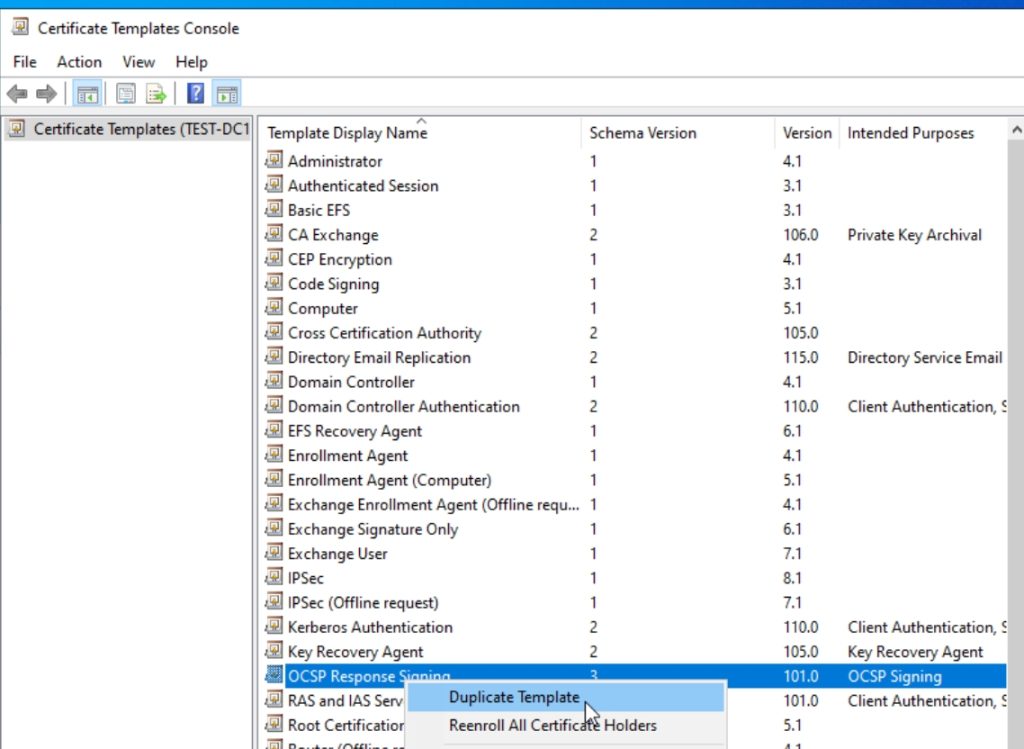
New window will pop-up and be positioned in Compatibility tab – under Certification Authority select Windows Server 2016, and in Certificate recipient select Windows 10/Windows Server 2016. If the pop-up appears, just confirm with OK. Stay in this window.
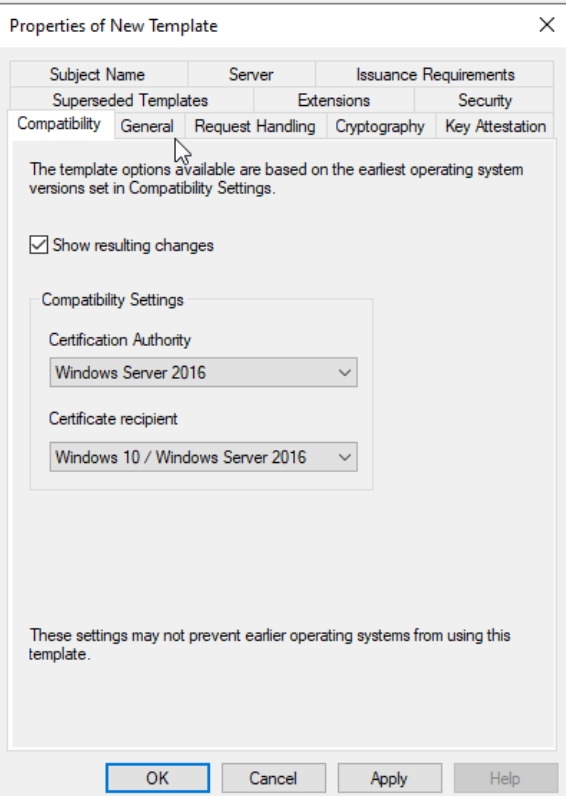
In General tab change the display name and leave everything else as is.
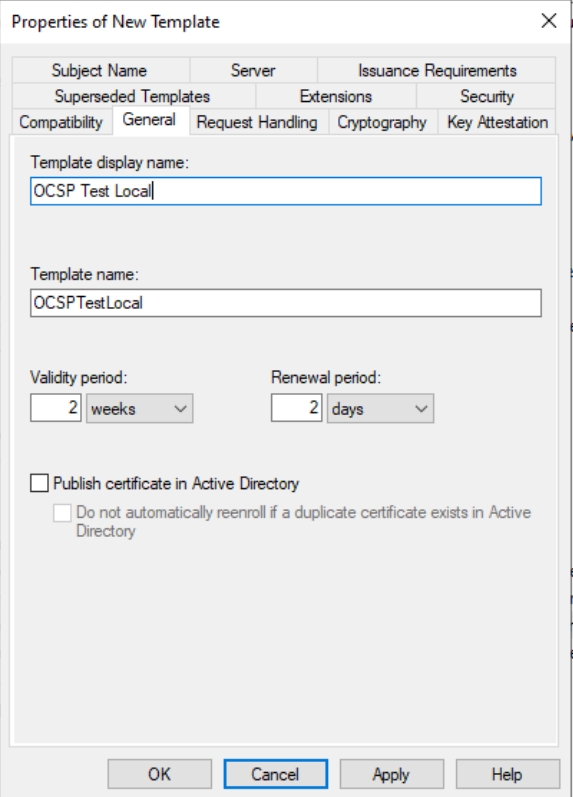
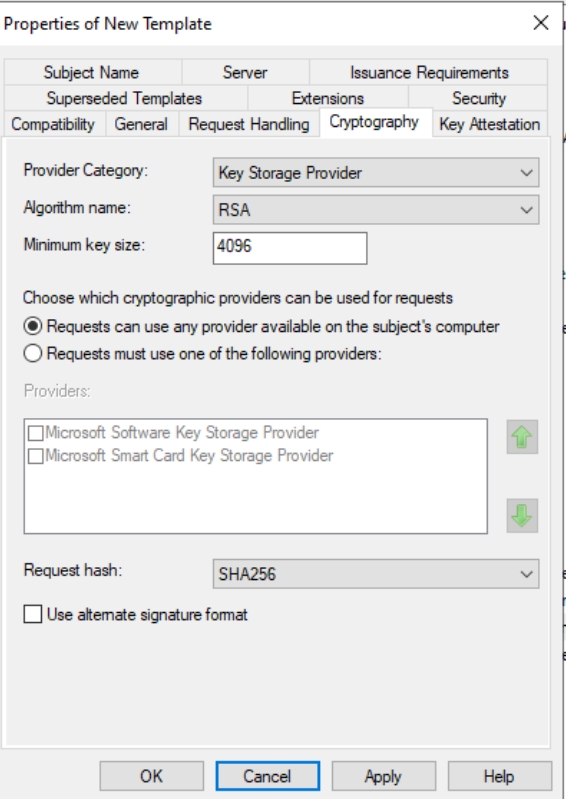
In Security Tab, change Minimum key size to 4096 and Request hash to SHA256.
In security tab – select Authenticated Users and enable Enroll permission.
Also add your CA1 server and enable Read and Enroll Permissions.
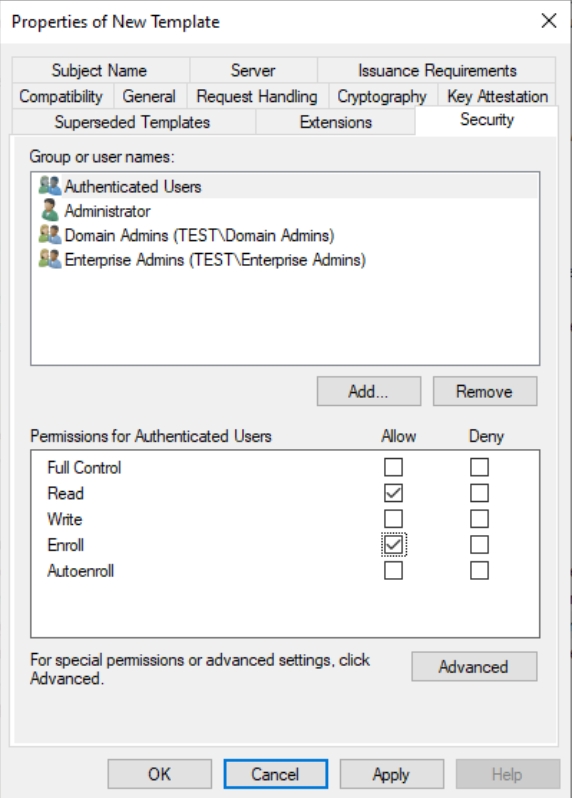
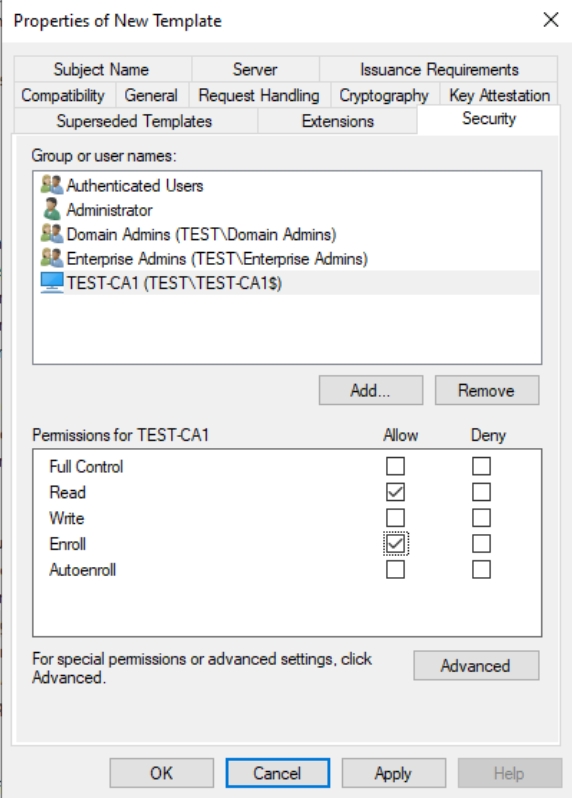
Now click on Apply – OK to close the window. We now have our Template added and listed. Close the Certificate Templates console and stay on Certificate Authority console.
Right Click on Certificate Templates again and select New –
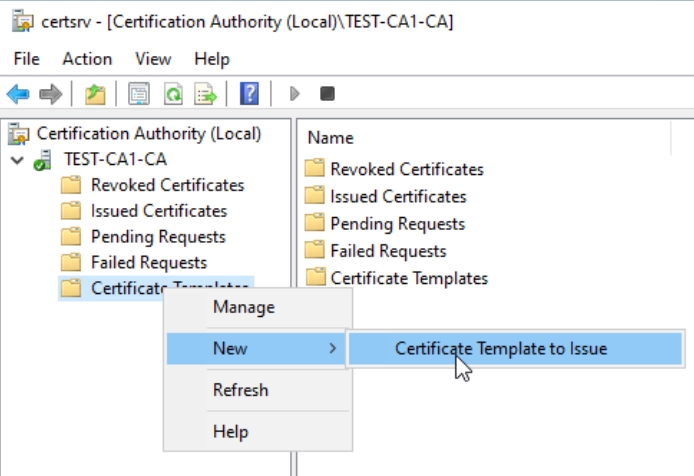
I will select template I created – OCSP Test Local and press OK
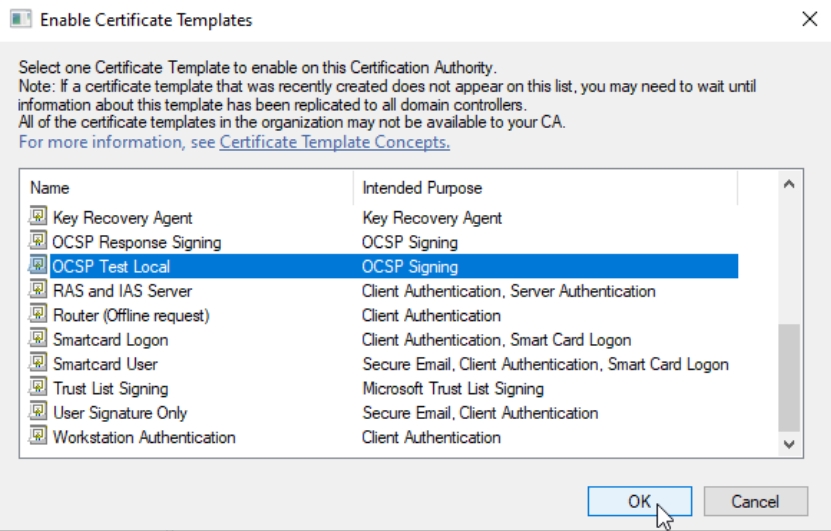
That Template is now listed in Certificate Templates
Revocation Configuration
Let’s now configure revocation on CA1 server.
We will now open Online Responder Management console by typing into search ocsp.msc on CA1 server
Right click on Revocation Configuration and click on Add Revocation Configuration
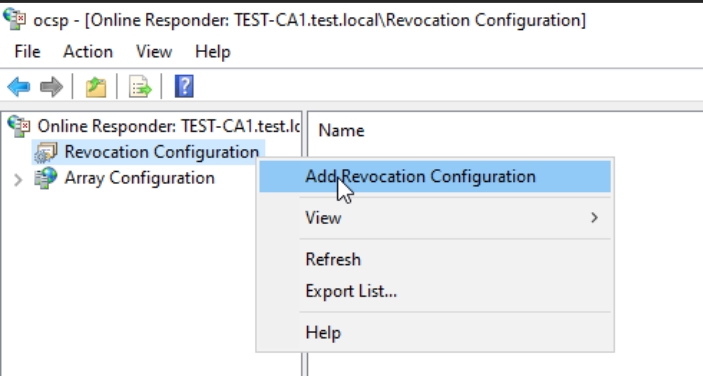
On the first screen, steps will be presented to you. Press Next
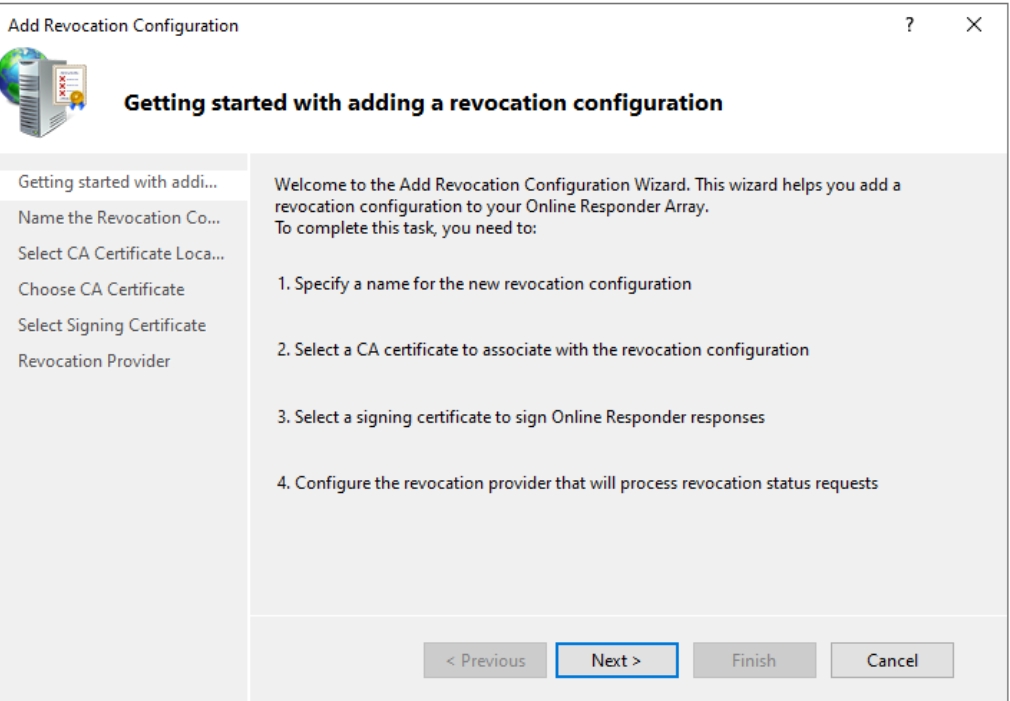
I’m terrible with names, so select what you wish and press Next
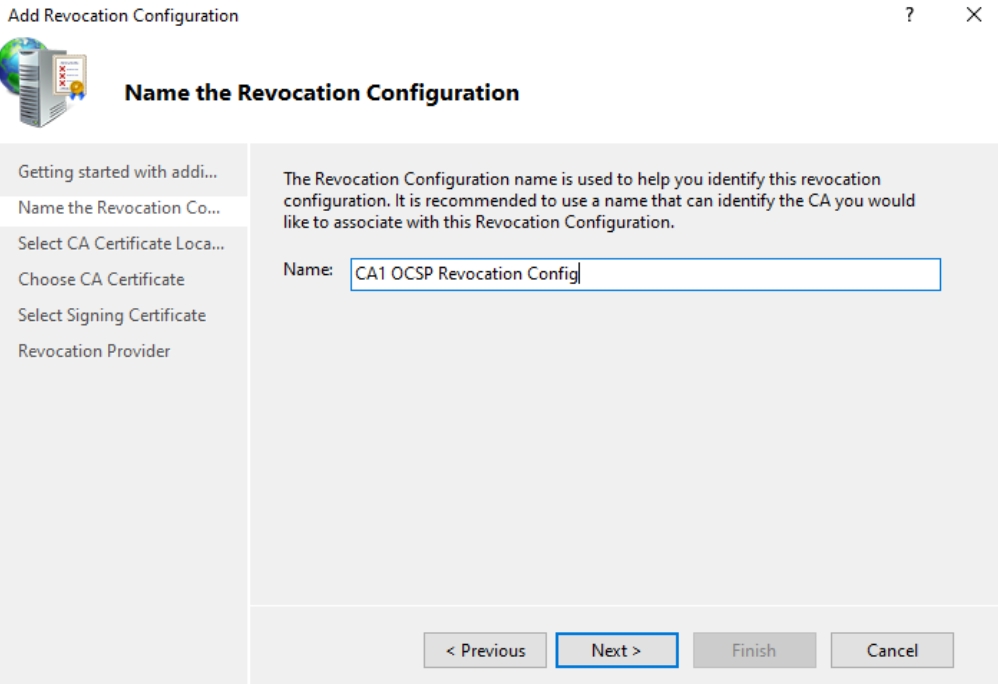
Select a certificate for an Existing Enterprise CA
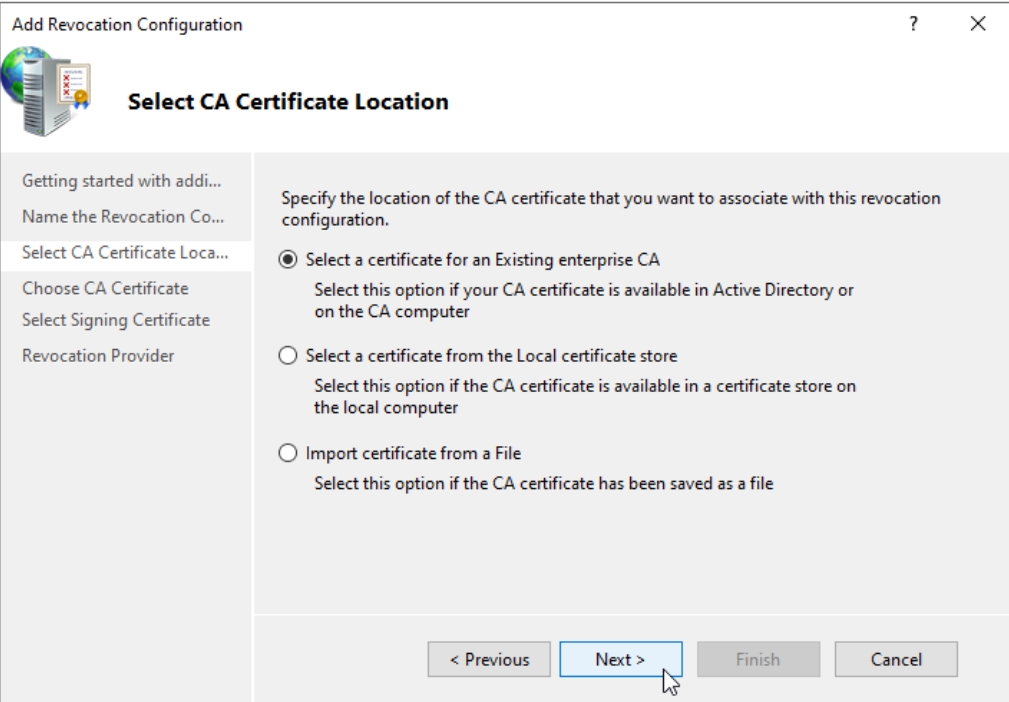
Browse CA certificates published in Active Directory
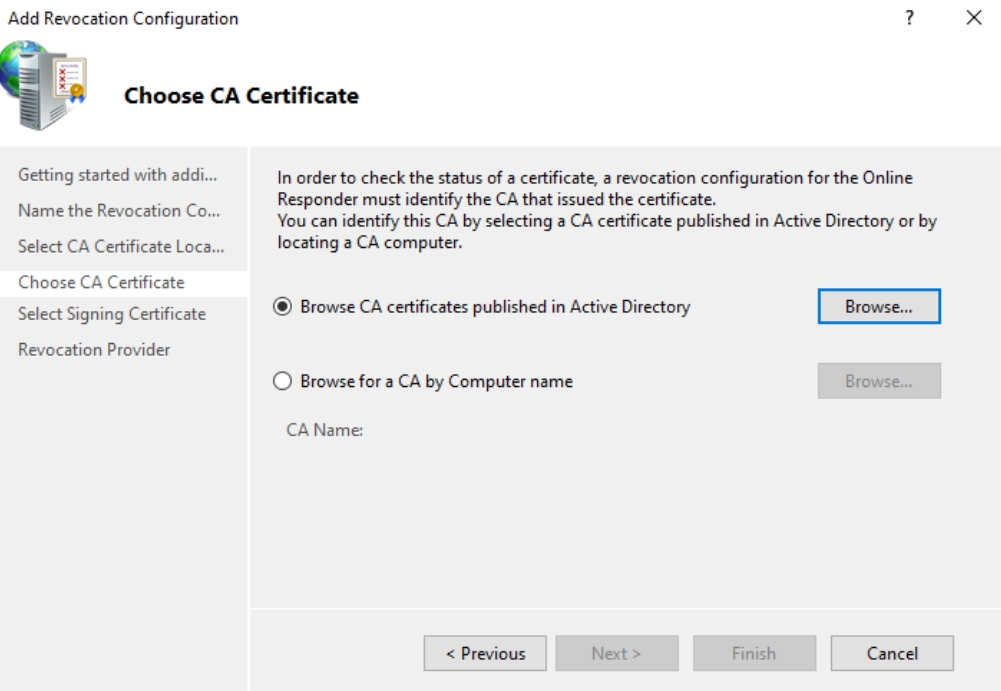
You should be offered a certificate. PRess OK and Next
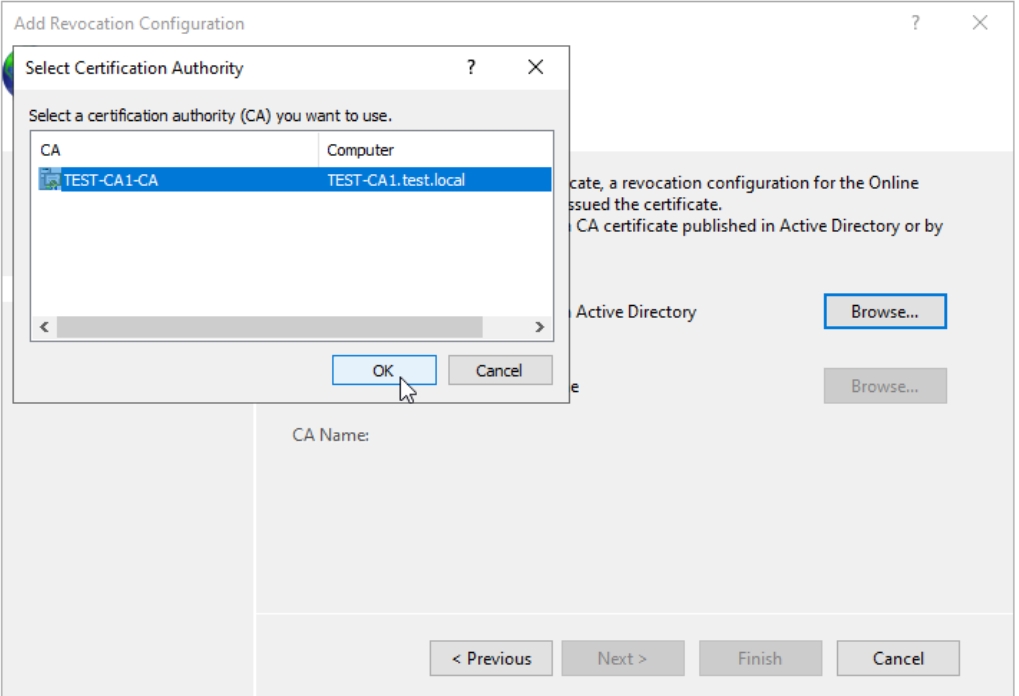
Use default options and press Next
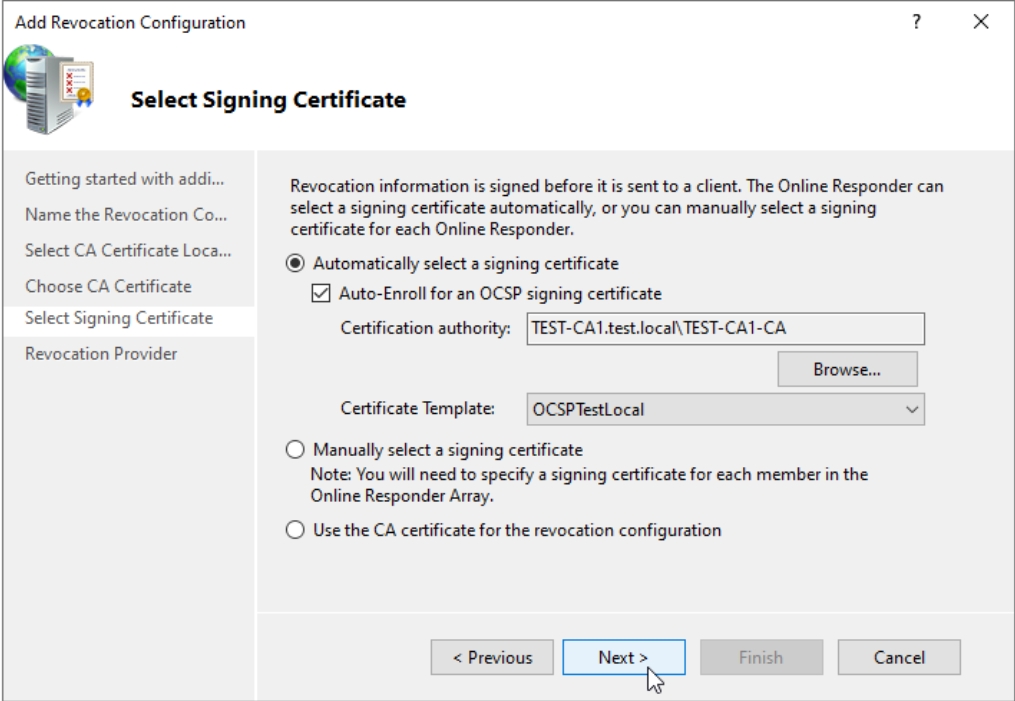
On Next screen click the Provider button
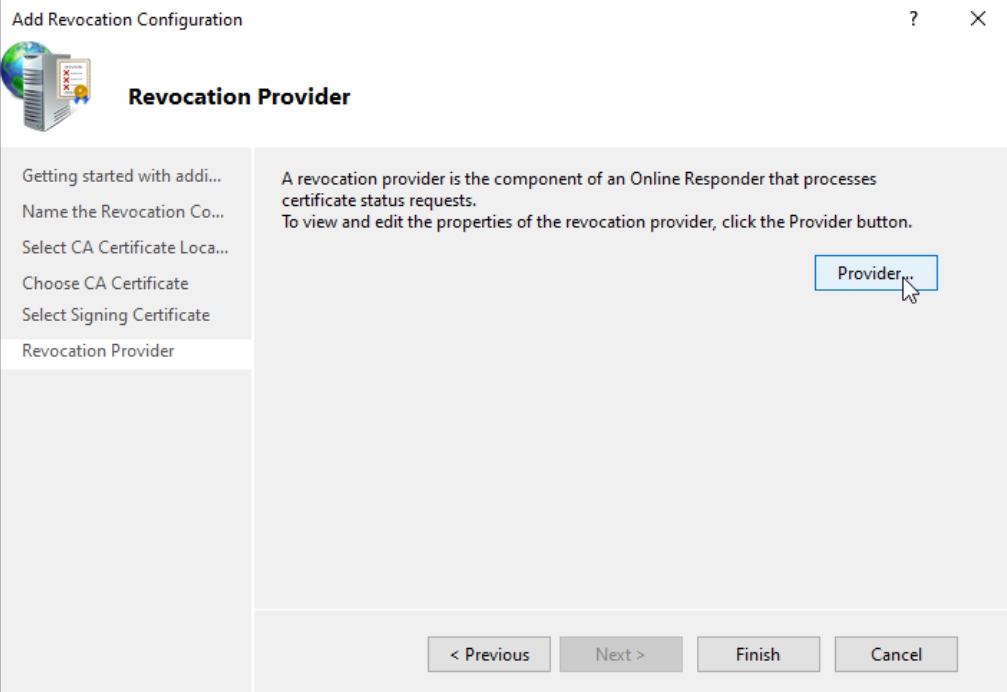
For both LDAP and HTTP values uncheck Refresh CRLs based on their validity periods and in Update CRLs at this refresh interval (min) enter 15 minutes. Press OK.
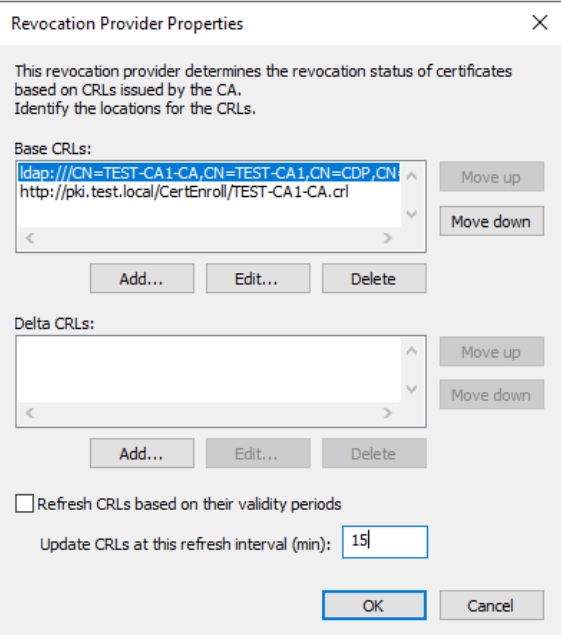
Press Finish
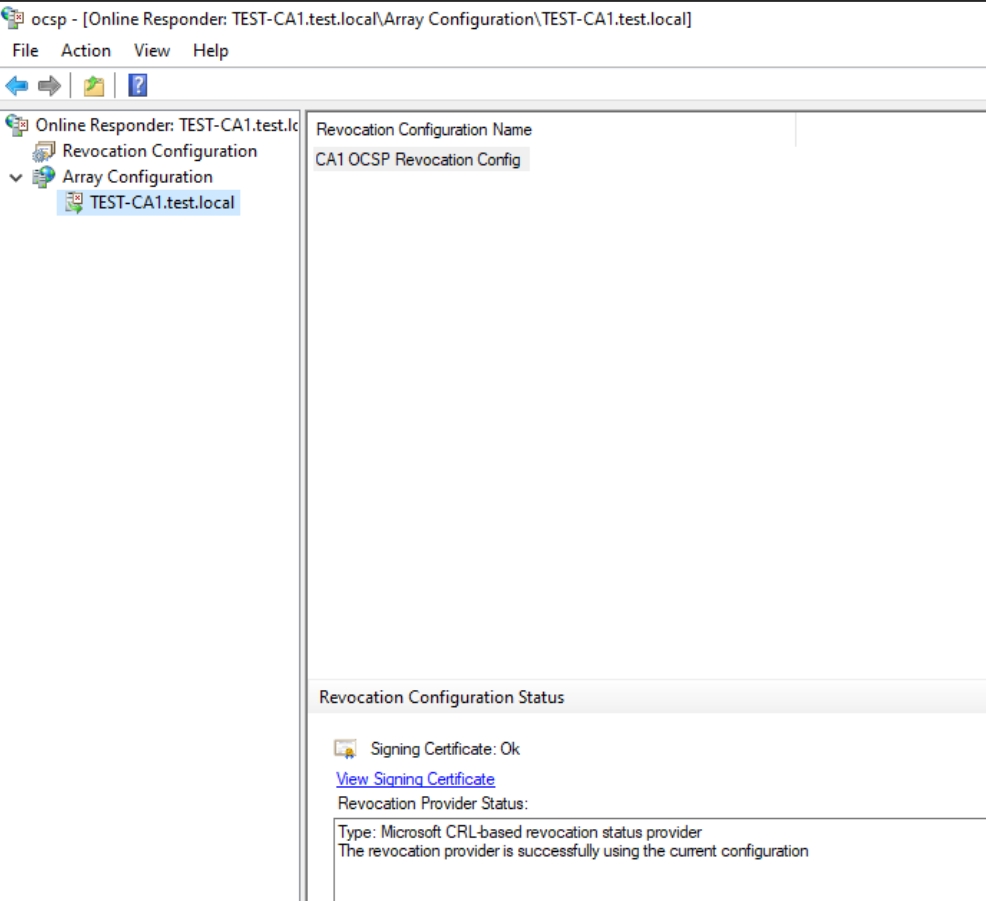
If we expand Array Configuration and select Test-CA1.test.local – signing certificate should be ok, and should be successfully using the current configuration.
Ok, but don’t yet close OCSP Management Console
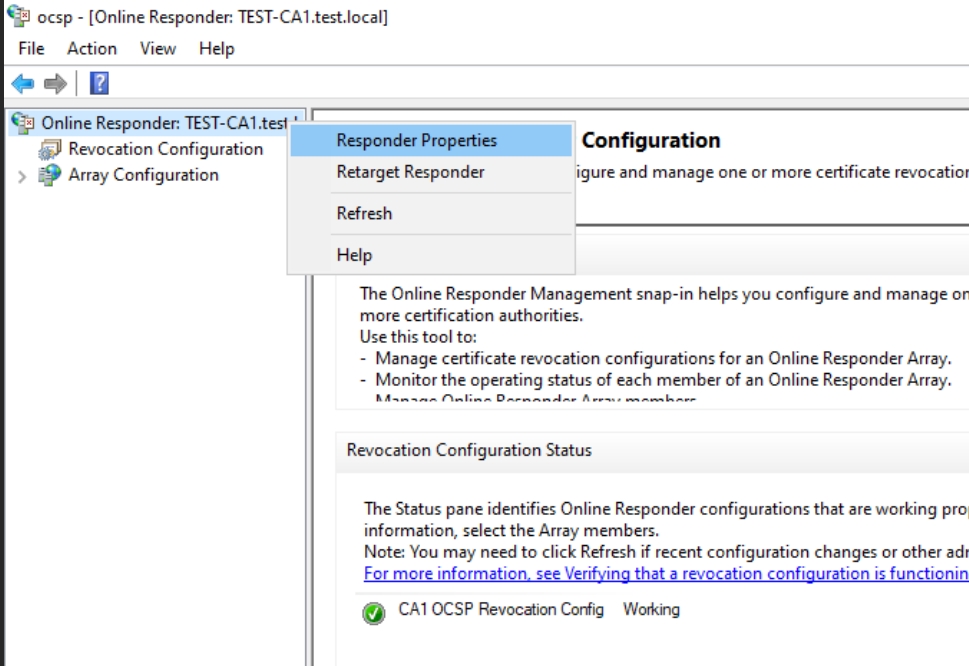
Enable Auditing on the Online Responder
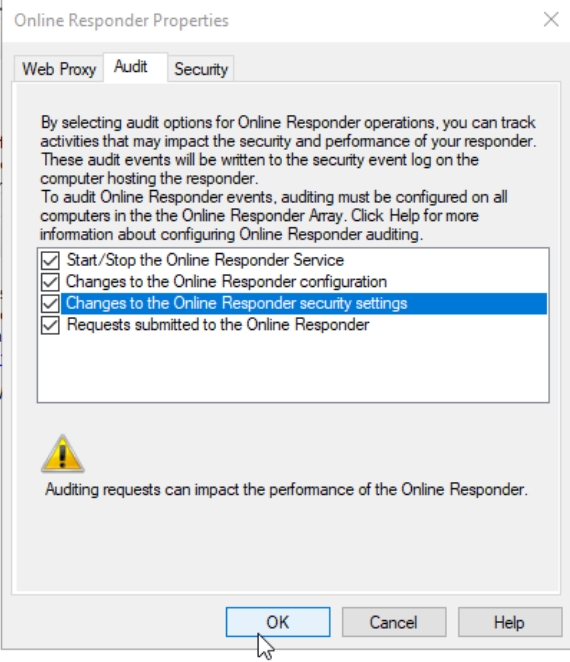
Right click on Online Responder at top of the window and select Responder Properties
On Audit tab select all fields, and press OK. All events will appear in Event Viewer under Security. We are looking for Event IDs between 5120 and 5127.
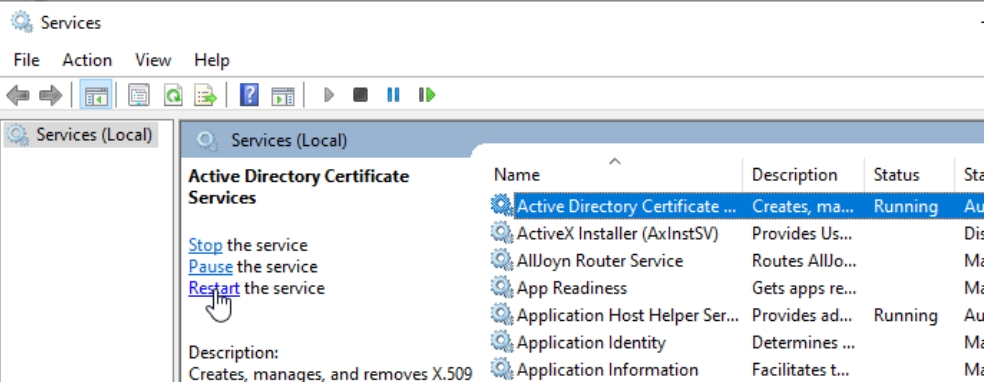
Restart Active Directory Certificate Services for this to take action
Add OCSP URL to Group Policy
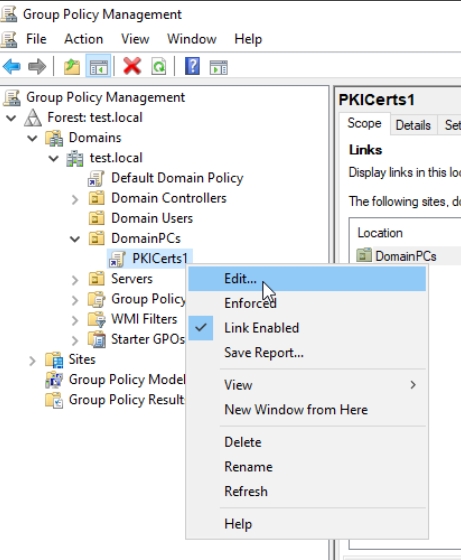
This id done on domain controller – DC1 – Open gpmc.msc and select OU where you wish to add gpo for OCSP.
We will expand created PKICerts1 policy we created at part 3 and click on Edit
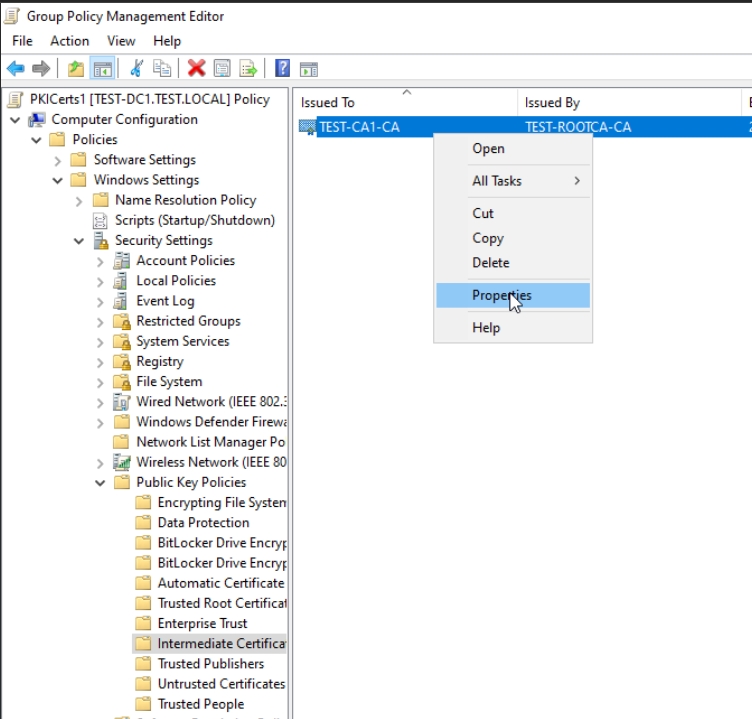
Open Computer Settings | Policies | Windows Settings | Security Settings | Public Key Policies | Intermediate Certification Authorities | Right click on CA1 cert and select Properties
Select OCSP tab and enter URL in the field next ot Add URL – I entered http://ocsp.test.local/ocsp and pressed Add URL – Apply OK
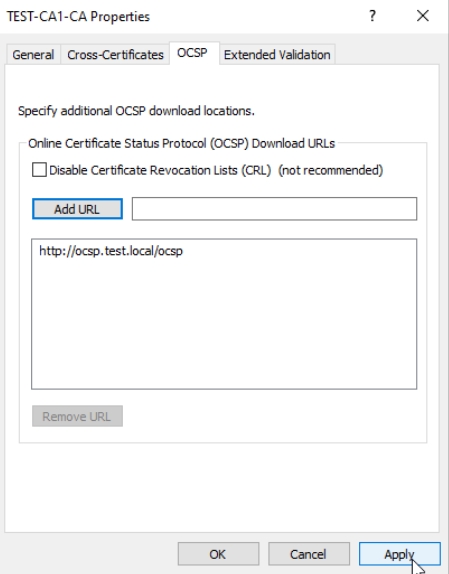
We are done now with Group Policy. Close everything and restart Active Directory Certificate Services service on CA1.
Deployment of this URL through domain can take up to one hour.
Verify OCSP Status
In search type in and open Enterprise PKI console (pkiview.msc).
We will now verify if Online Responder is working correctly.
Expand you node and server, and surprise, OCSP is red X.
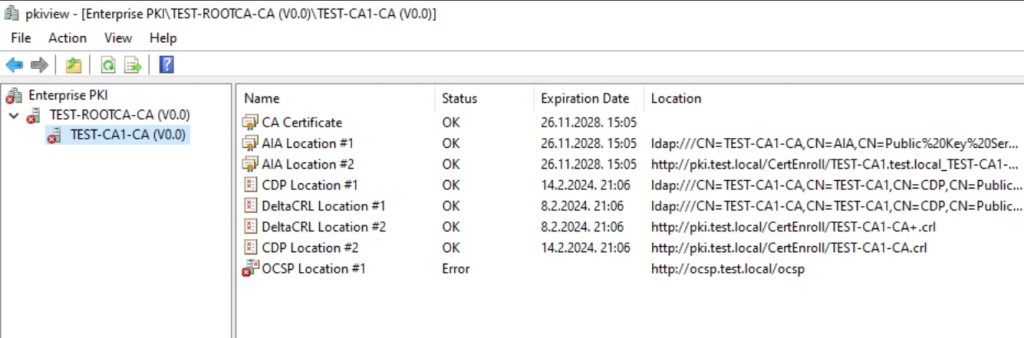
Ok, let’s check what is the problem.
We will open Certification Authority console also (certsrv.msc) on CA1 server. Navigate to Issued Certificates folder and look for the one named CA Exchange. I have two, I will right click on each one of them and select All Tasks – Revoke Certificate – leave everything as is under Reason code – Yes
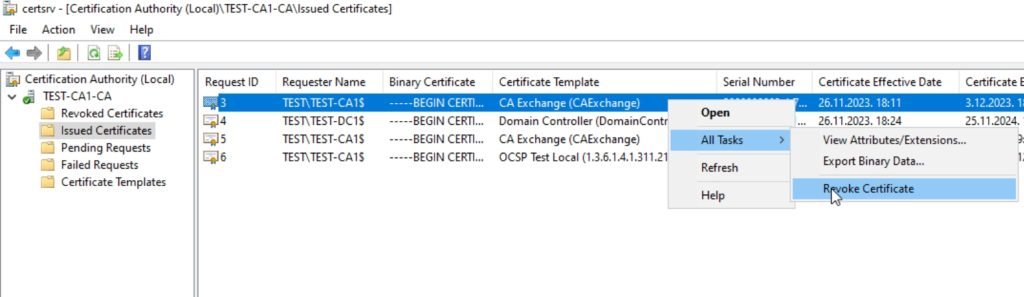
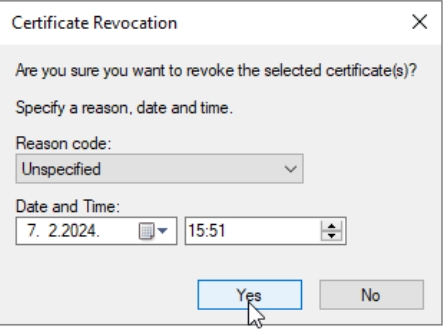
Now, open Powershell as admin and type in following
certutil.exe -cainfo xchg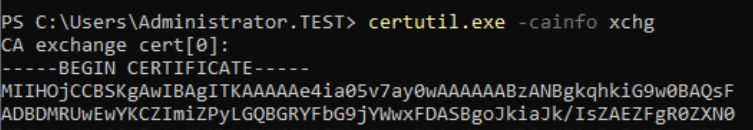
If we go back to Enterprise PKI console (pkiview.msc) and have a look, no more red Xs, everything is fine.
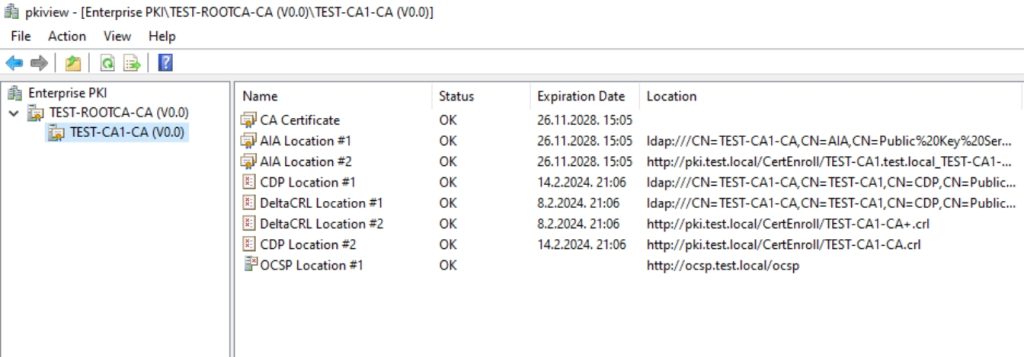
Problem was with CA Exchange certificate. It was generated before Online Responder was configured, and it needs to be recreated to be valid. Fortunately not a great issue, since PKI in itself is really complicated matter.
Test OCSP connectivity
Ok, we need to test if the Online Responder works and can communicate through domain. Will will export and analyze certificate through URL Retrieval Tool. We will also verify CA and CRL location with this test. We will start on CA1 server.
I will export CA1 cert into C:\ and name it C:\CA1cert.cer. I will export it without private key.
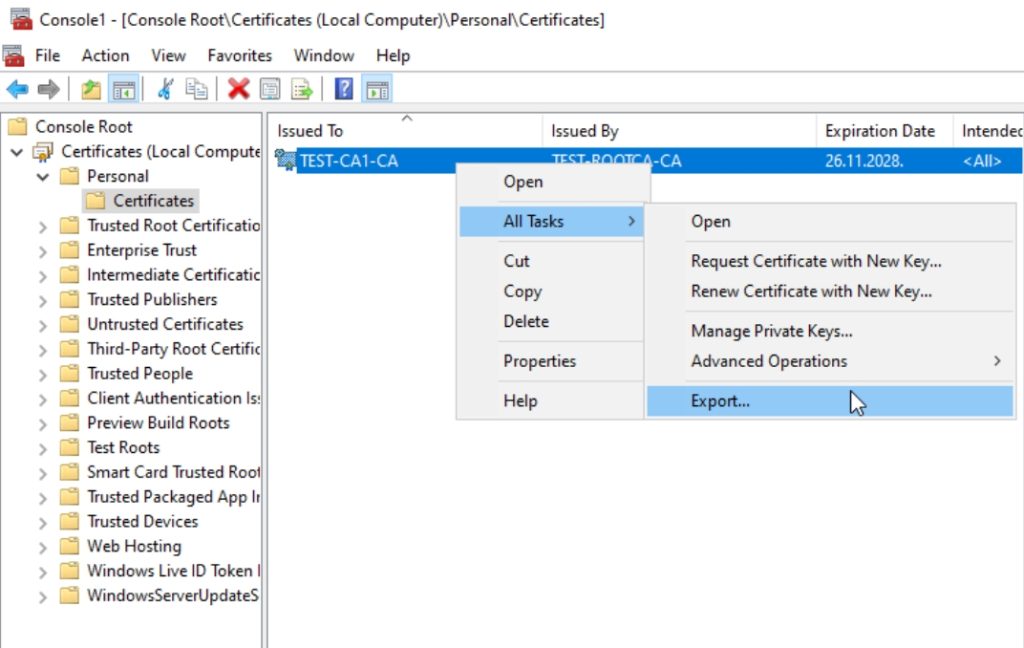
Next, we will start Powershell elevated on CA1 and type in following command (change location and name of the cert with your own)
certutil.exe -URL "C:\CA1cert.cer"URL Retrieval Tool will pop-up
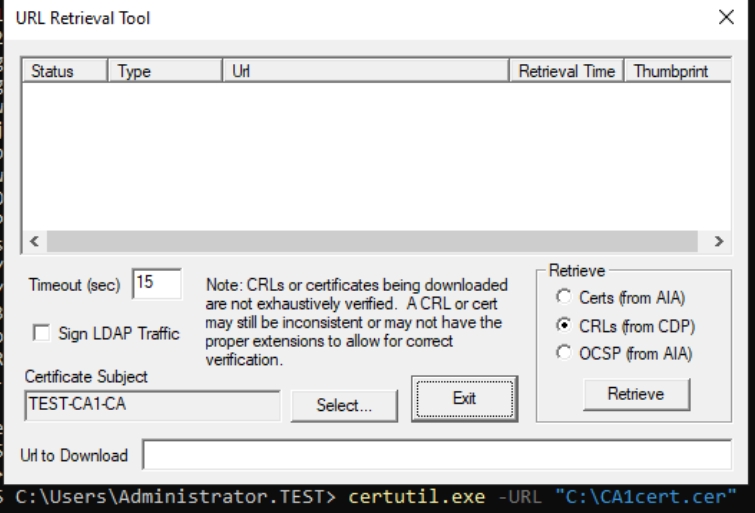
Let’s now begin testing, certificate is loaded, in Retrieve field select Certs (from AIA) and Press Retrieve, locations should appear, and status should be Verified.
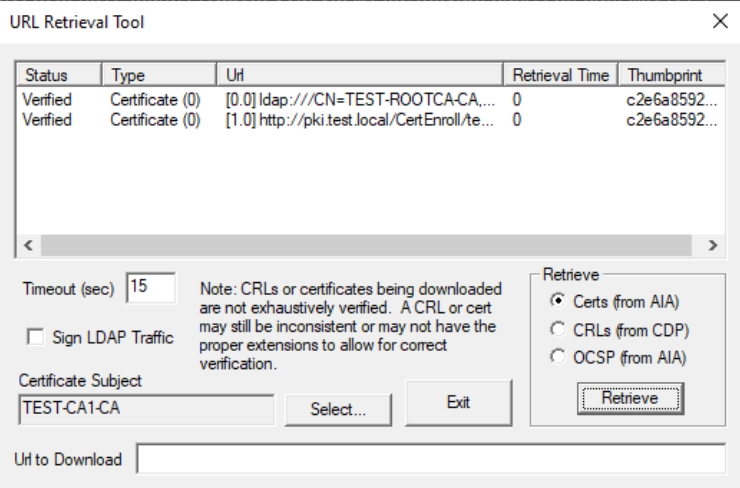
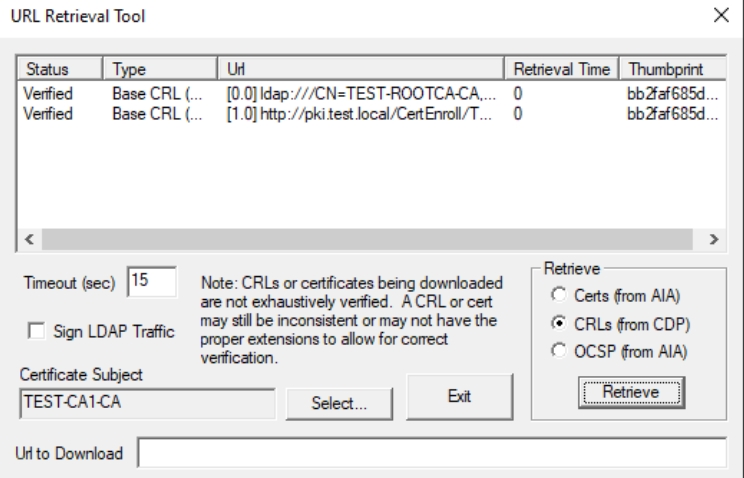
Repeat the same for CRLs (from CDP) and OCSP (from AIA), you should get links, and all should be verified.
For CDP everything is ok.
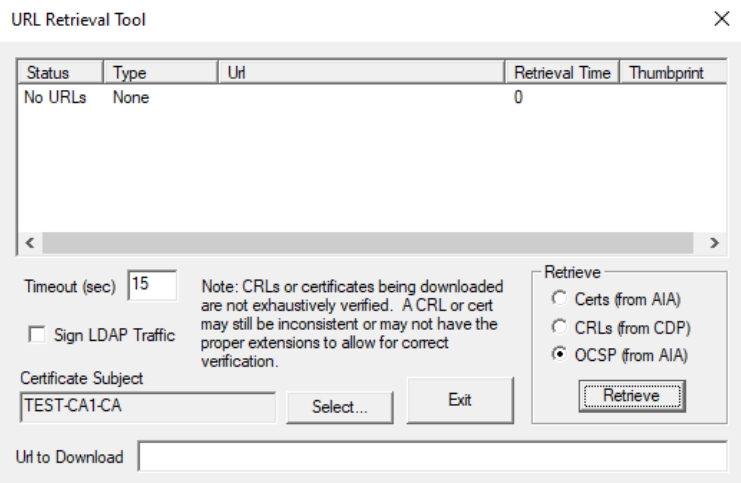
For OCSP (from AIA) I got none as a result. This should not yet be reason for concern since other tests are fine and no errors are shown in OCSP or PKI Manager console. Previous tests were fine, we will wait a bit more until AD propagation lives that we mentioned earlier. Few hours later I still got No URLs and will get back to this. After few days I still don’t have URL here, although everything works ok. If you have something on this topic, please share with me.
This is all for OCSP. You should be aware that OCSP has to be maintained and can cause issues. You should check on OCSP role once in a time to confirm that the role is working and healthy. Also, be aware, that sometimes soon after you reboot, ocsp.msc and pkiview.msc can give you OCSP errors and ugly red Xes, just be patient and wait a bit until everything goes through, services start and they become aware of domain and services…
Implementing Two-Tier PKI on Windows Server 2022 – Part 1
Implementing Two-Tier PKI on Windows Server 2022 – Part 2
Implementing Two-Tier PKI on Windows Server 2022 – Part 3
Implementing Two-Tier PKI on Windows Server 2022 – Part 4 – you are here
Implementing Two-Tier PKI on Windows Server 2022 – Part 5
Implementing Two-Tier PKI on Windows Server 2022 – Part 6
Implementing Two-Tier PKI on Windows Server 2022 – Part 7