This will be closing part of the PKI series, we will look into topics such as – removing old certificate authorities, reissuing Root CA CRT, backing up, and so on…
Before implementing CA, in your AD you should check if there already were former Certificate Authorities. I had instances where somebody set CA, and forgot about it. It should be removed before we put new certificate authority in production.
Remove Ex Certificate Authorities
So, we will first look at that, what to do, if there were Certificate Authorities on domain that are no longer maintained, and will make trouble with our new implementation.
On DC in your domain check following:
Open Active Directory Sites and Services (dssite.msc). First thing we will do is select Show Services Node
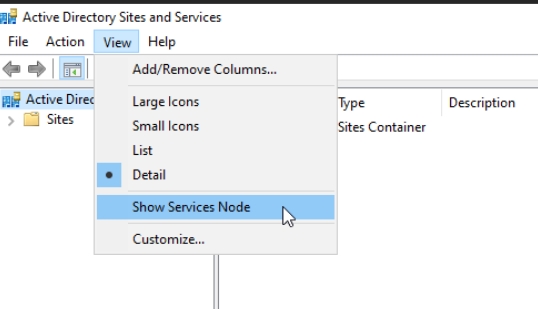
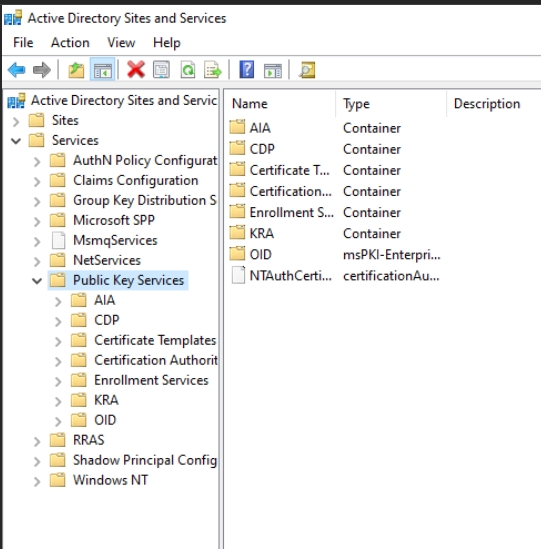
Expand Services – Public Key Services
You should check AIA, CDP and Certification Authorities maps – there should be no references to Root CA or Subordinate CA in those. (Don’t DELETE anything!!)
You can also check those by running following command in Powershell (as admin)
certutil.exe -dumpYou can also look at Group Policy to see if there is anything in there.
Now, if there is something in these locations, that means there is or was a CA on a domain. To decommission it, look into Microsoft documentation – https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/decommission-enterprise-certification-authority-and-remove-objects
This guide will just be way too long to describe every possible situation.
Renewing Root CA CRL
As we said in the part 1, turn on your Root CA server at least once every 50 weeks, and check it and renew BaseCRL.
To Renew CRL on Root CA,, do the following on Offline Root CA
Open Certification Authority console (certsrv.msc) on Root CA. Right click on Revoked Certificates and select All Tasks – Publish
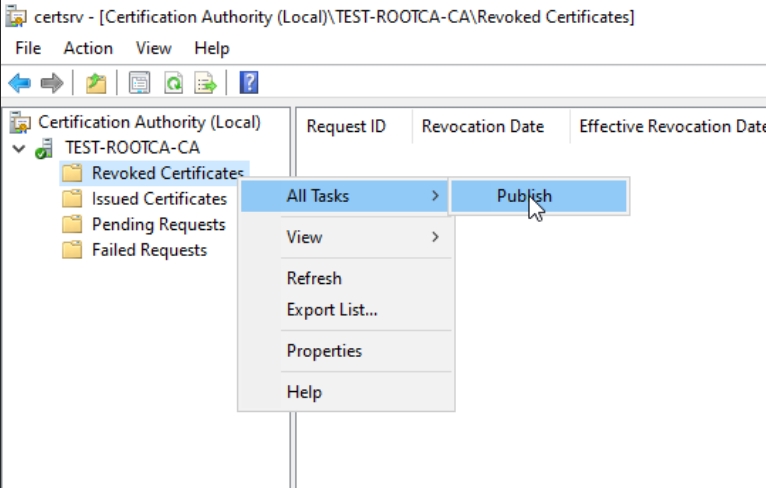
On the Publish CRL screen select New CRL and click OK. Close Certification Authority console.
You can also do the same through Powershell (as admin) by typing in following
certutil.exe -crlNow, we need to copy new .crl file from C:\Windows\System32\CertSrv\CertEnroll folder to C:\RootCA folder (overwrite existing if something is in there).
Copy C:\RootCA to virtualfloppy, vhdx, or whatever you consider secure and copy/transfer that to CA1.
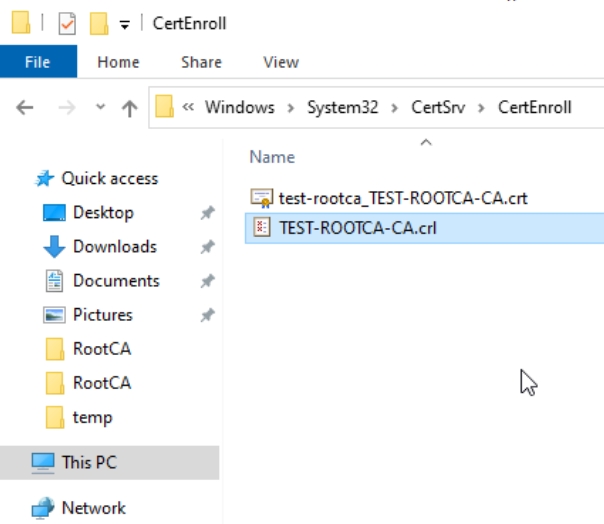
On CA1 server we need to copy new .crl file to C:\CertData folder (overwrite existing).
Next, on CA1 we need to publish new Root CA crl to AD. To do so, execute following in elevated Powershell
certutil.exe -addstore -f root "C:\CertData\TEST-ROOTCA-CA.crl"
Important thing is not to forget this every year!! Add it to your calendar and make it most important task.
Manually Backup PKI infrastructure
We will do this on CA1 server. In root of C drive we will create C:\CABackup folder. Normally you need to backup this outside of CA1 machine – that is purpose of the backup. So be sure to have encrypted external drive or secure location where you will keep backup.
You should also backup regularly your entire environment, this should not be only backup you do. Schedule backups and check them!
On CA1 start Certfication Authority Console (certsrv.msc). Right click on server – All Tasks – Backup up CA…
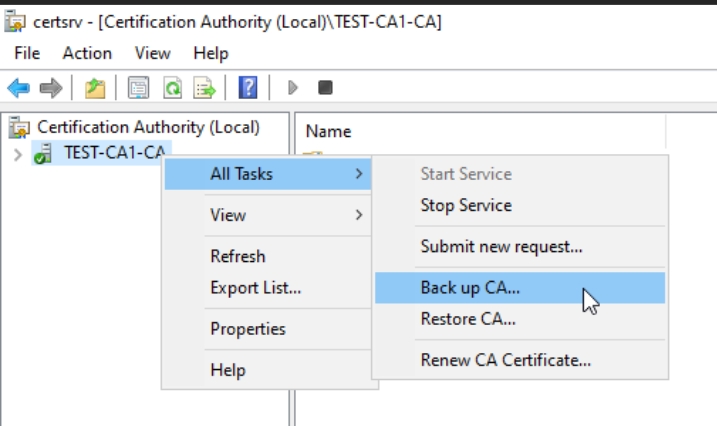
Next
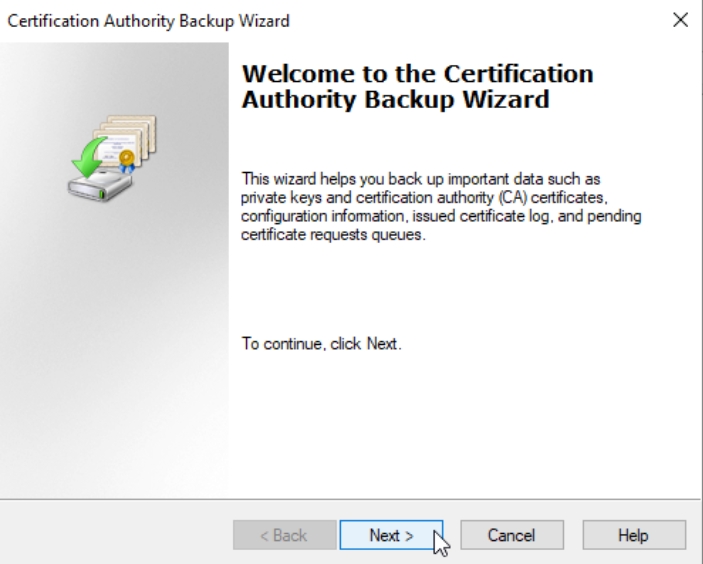
Make sure to select follwoing:
Private key and CA certificate
Certificate database and certificate database log.
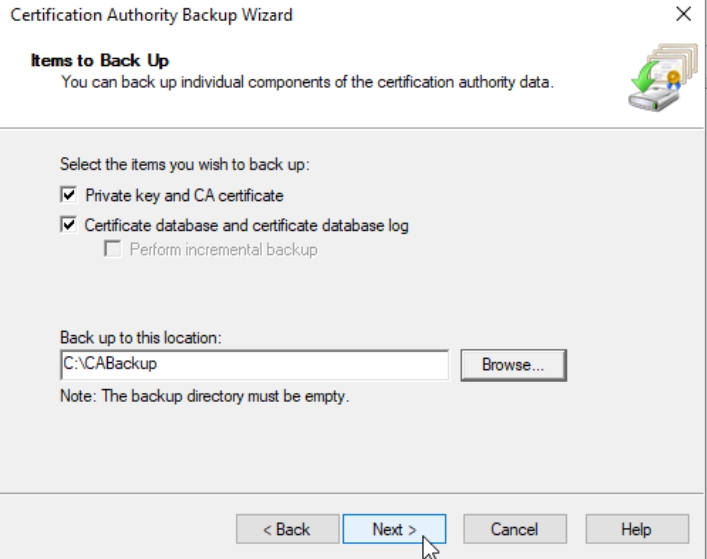
Select created C:\CABackup folder on CA1 server (in production this has to be somewhere of the CA1 server!!) Next
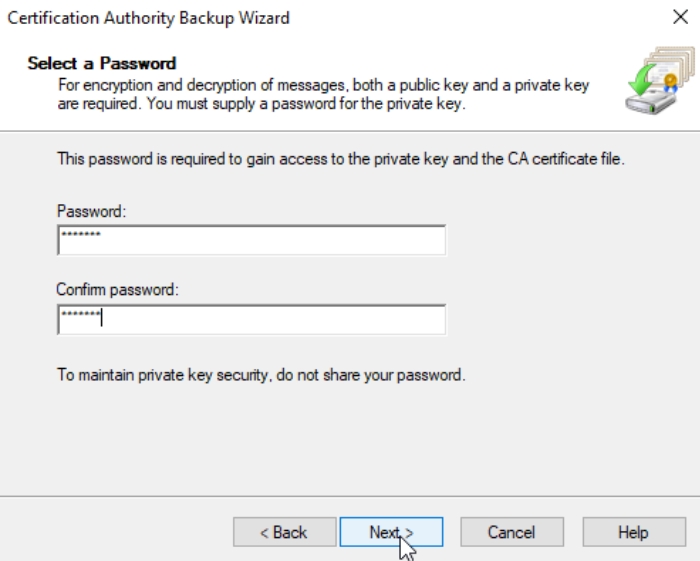
Define password (remember it, print it, keep it in safe!!) Next
Finish
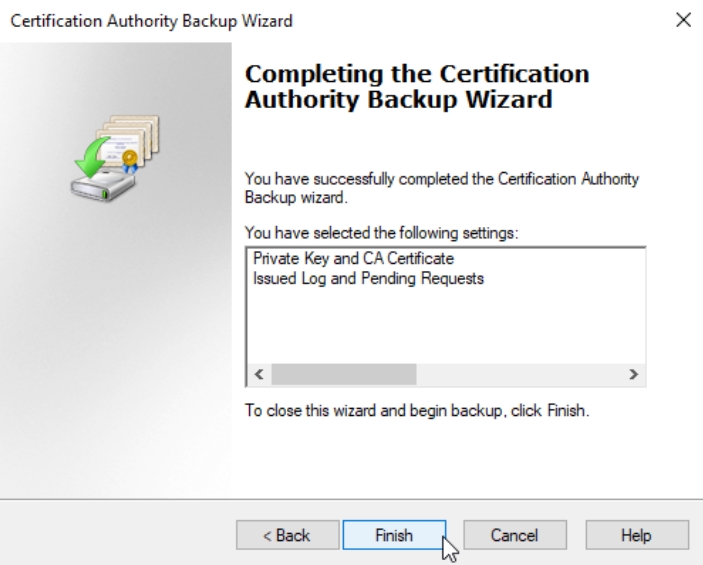
One more point we will visit on CA1 is registry
Open Registry Editor (regedit.exe)
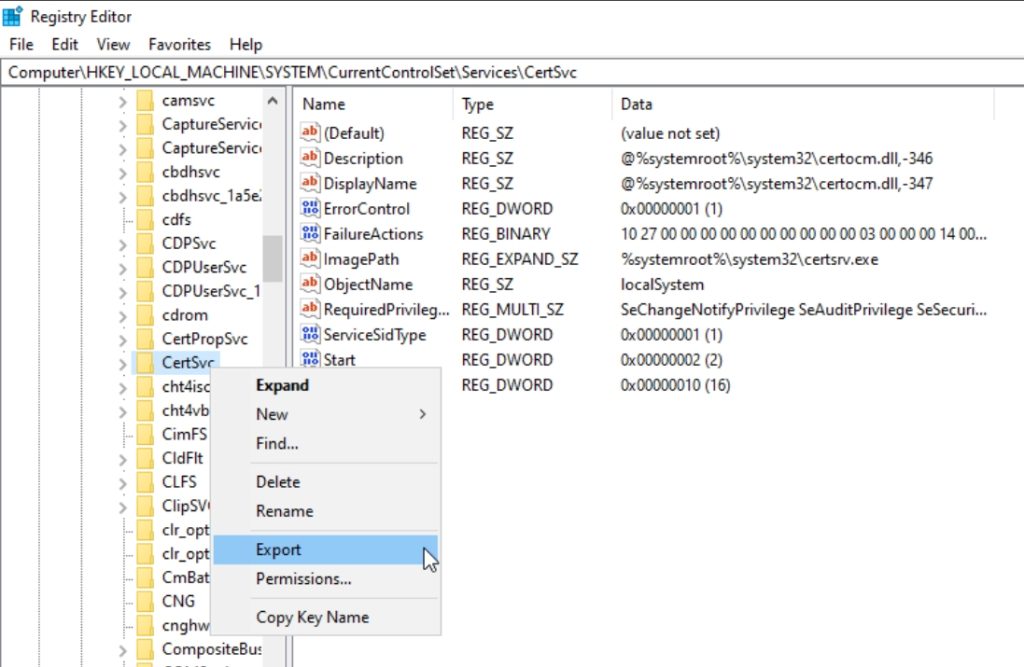
Navigate to HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\CertSvc
Right click on CertSvc and select Export
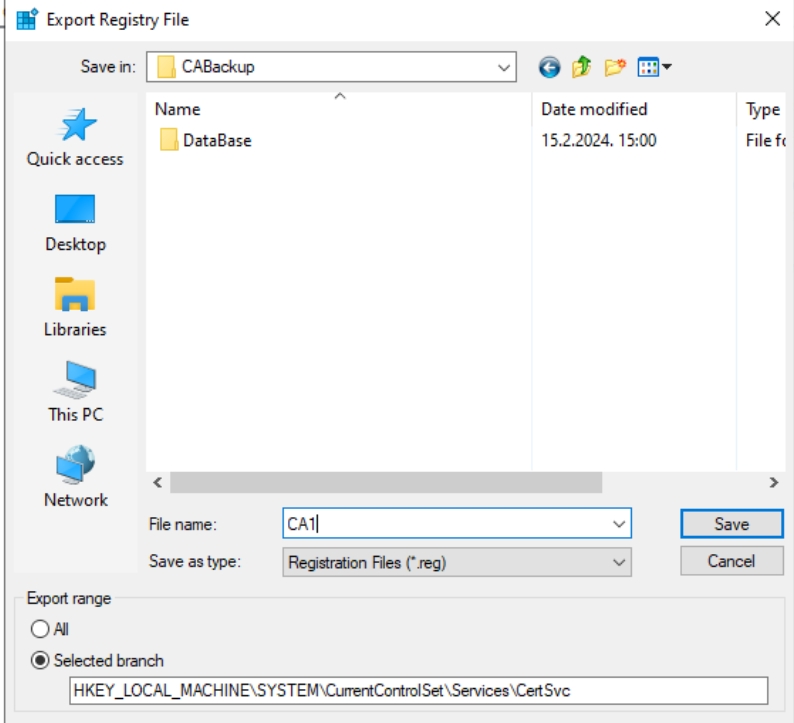
Again select C:\CABackup, give a name to a key and select Save
You can now close regedit
Your C:\CABackup folder should now look like this
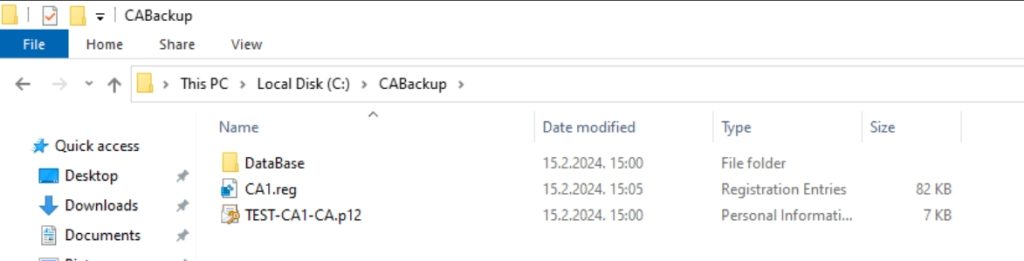
And that is that. We are now done with the entire PKI series.
You can check other parts of the series if you haven’t already
Implementing Two-Tier PKI on Windows Server 2022 – Part 1
Implementing Two-Tier PKI on Windows Server 2022 – Part 2
Implementing Two-Tier PKI on Windows Server 2022 – Part 3
Implementing Two-Tier PKI on Windows Server 2022 – Part 4
Implementing Two-Tier PKI on Windows Server 2022 – Part 5
Implementing Two-Tier PKI on Windows Server 2022 – Part 6
Implementing Two-Tier PKI on Windows Server 2022 – Part 7
Implementing Two-Tier PKI on Windows Server 2022 – Part 8 – you are here