After successful installation –https://www.informaticar.net/how-to-install-pfsense-on-hyper-v/ and initial configuration https://www.informaticar.net/how-to-configure-pfsense/ you have working firewall. But now if you would like to customize it and block something, there are few more steps that need to be done.
LAN rules are defining rights to access internet services from your local network. So, if you block port 80 and 443 nobody from your LAN will be able to access internet.
WAN rules are defining access to the resources in your LAN (or DMZ) from the internet.
In this short LAB we`ll be defining LAN rules.
Let’s say we want to block access to the port 443 from our local network.
My blog is on port 443, so after defining this rule we should not be able to access my blog from LAB network (or any other HTTPS secured website for that matter)
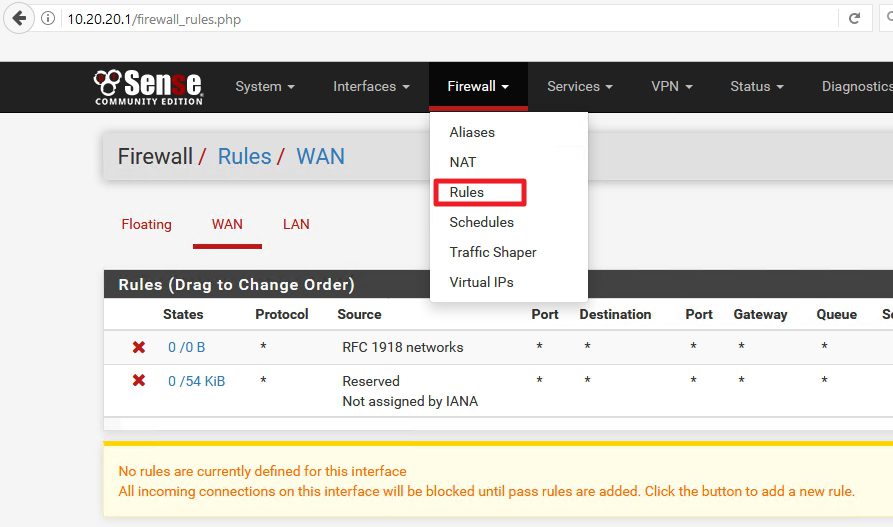
Login to your pFSense configuration via web browser – mine is is still located on http://10.20.20.1/
Select Firewall | Rules
Select LAN tab
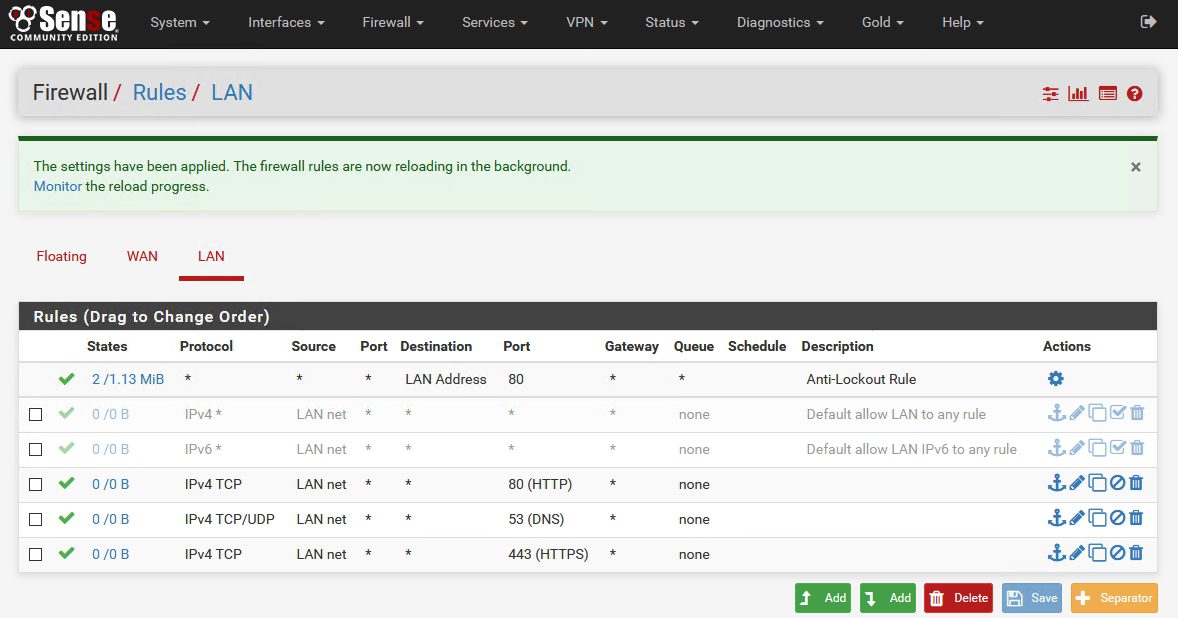
As you can see, by default all traffic from you LAN is allowed toward internet.
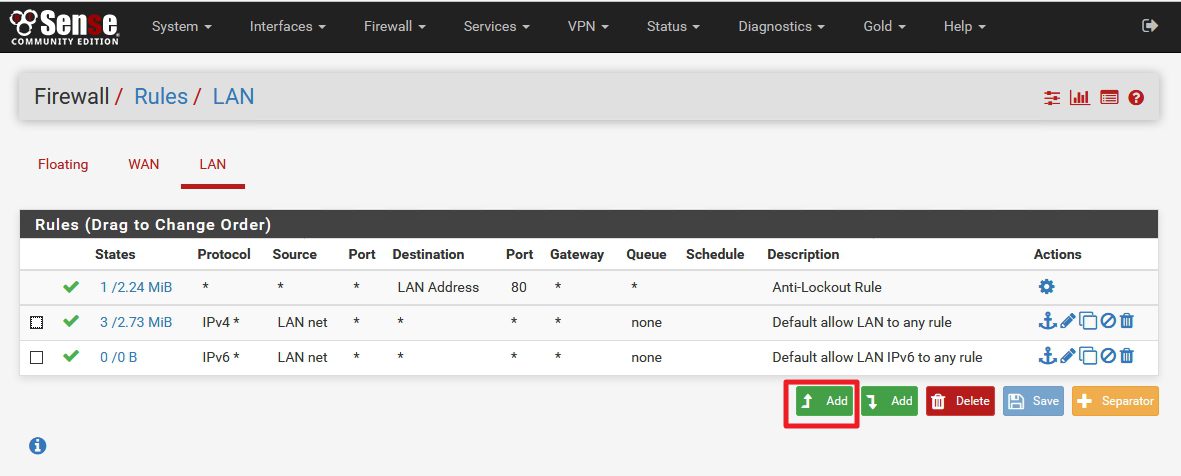
Select (up) Add
New window opens with settings:
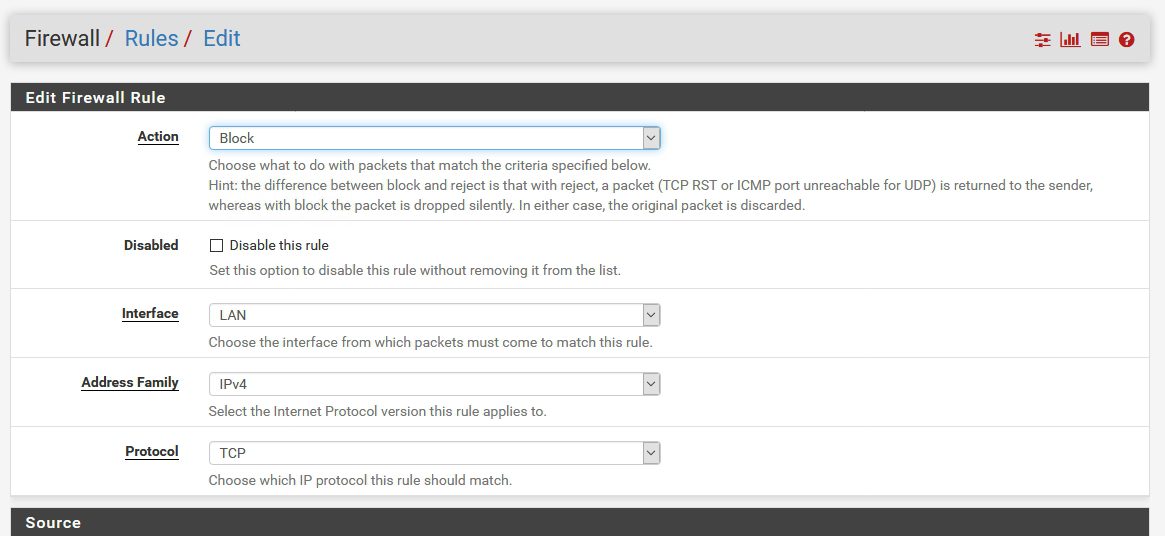
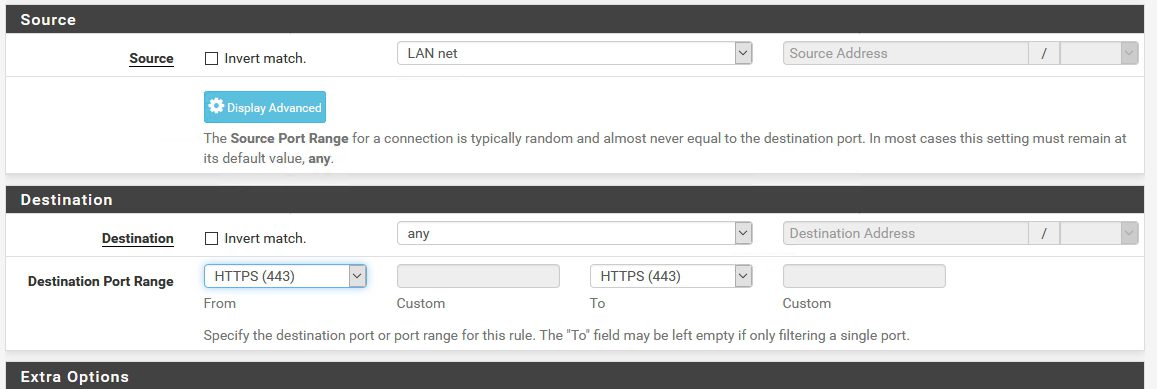
Action: Block (since I want to block traffic to the outside) | Interface: LAN | Address Family IPv4 |Protocol TCP
Source – that should be LAN net (we want to block HTTPS for whole LAN) |Destination: any | Destination Port Range HTTPS 443
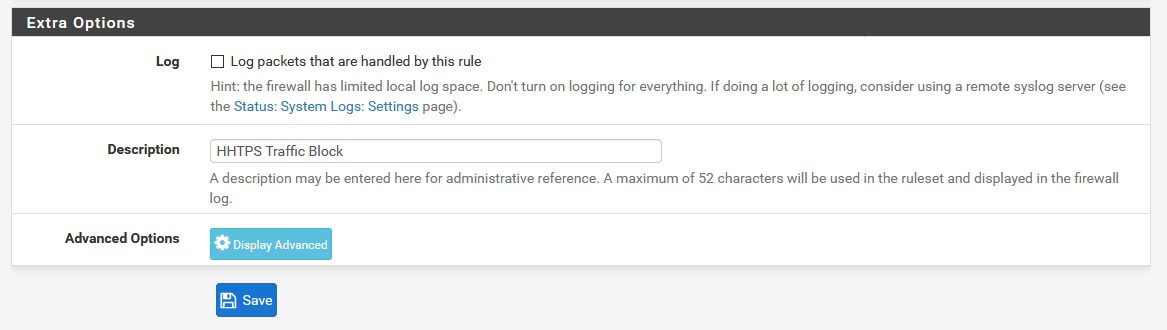
Extra Options: You can enter Description and turn on Logging for the rule | Save
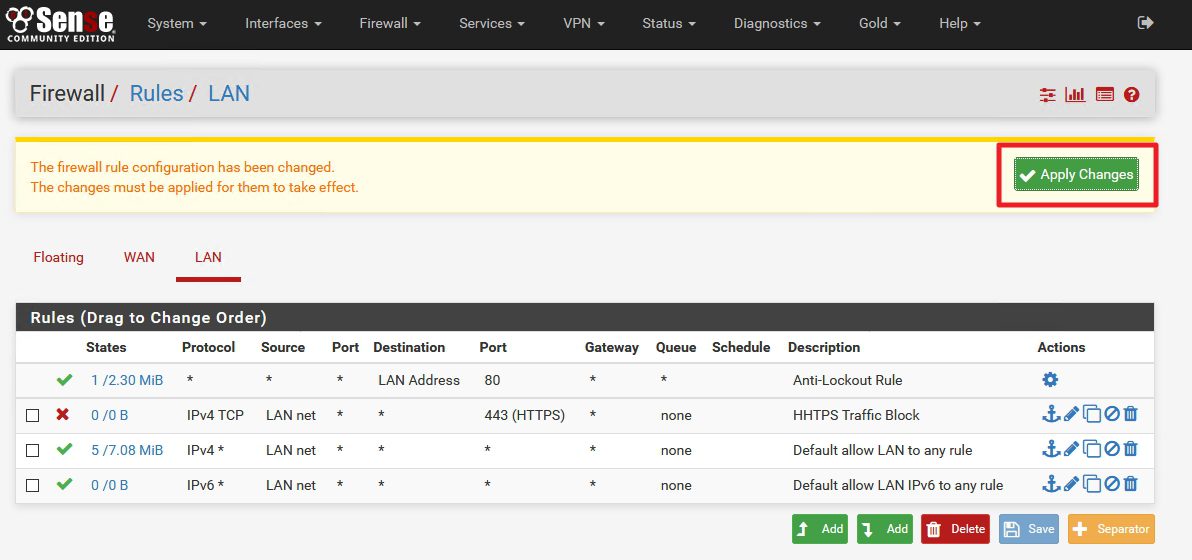
After you clicked on save you`ll be back on the main LAN Rule screen
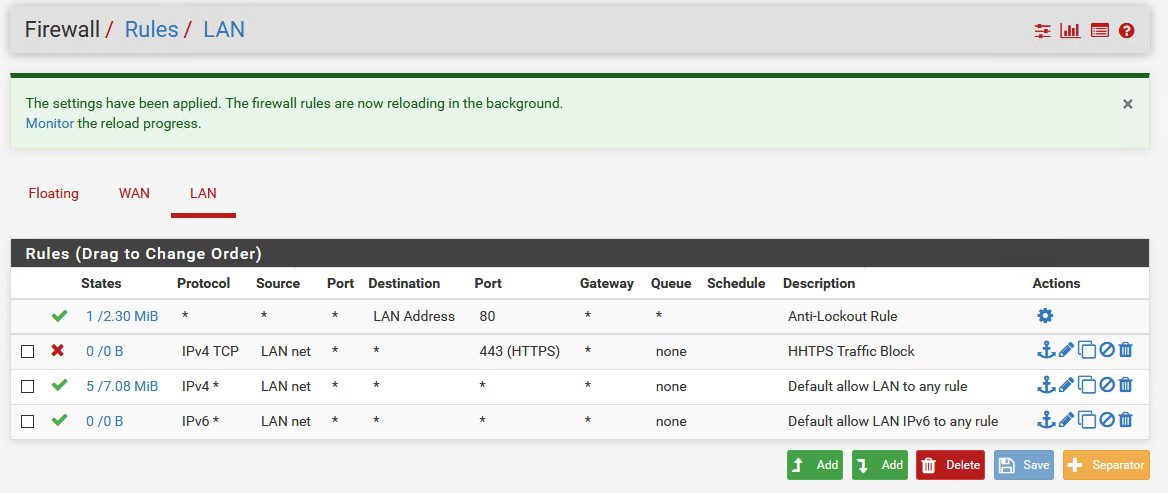
Click Apply Changes
Now, onto rule testing…
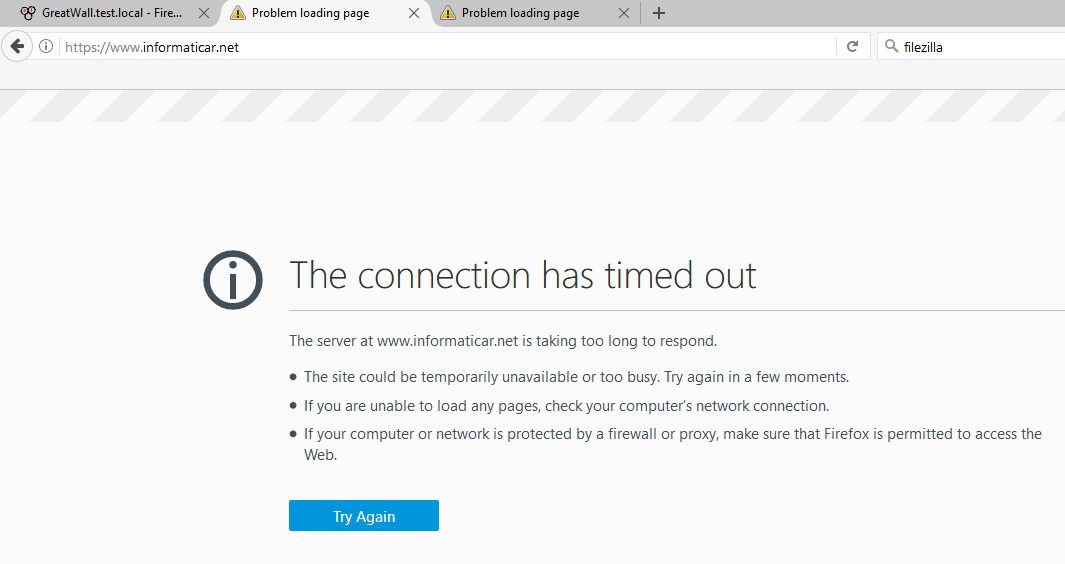
We should not be able to access my blog because it is on HTTPS protocol – https://www.informaticar.net/
Timed out…
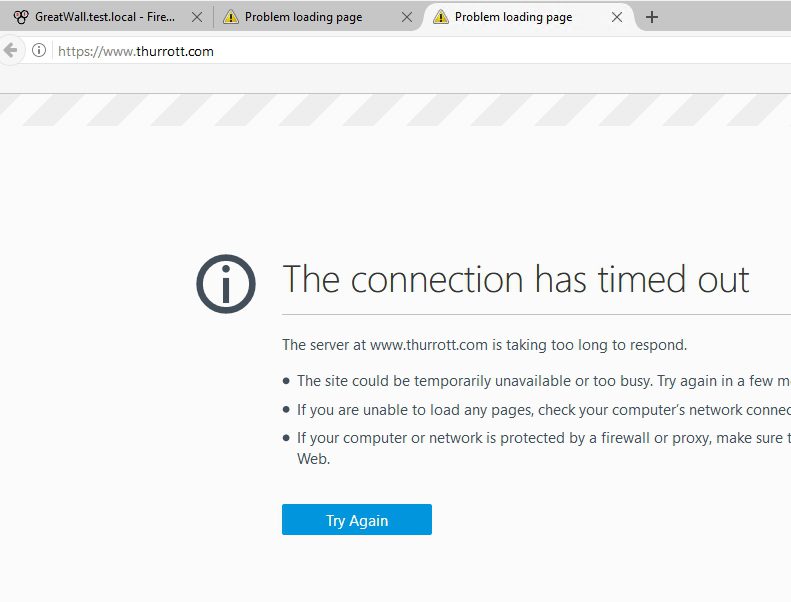
I also tried another site on HTTPS and result is the same
But, when we try site that is not HTTPS encrypted…
Works.
I also tested with FTP port – result is the same – so we can conclude that this works.
Smart idea would be to disable default ALLOW ALL traffic rules– you should remove default LAN firewall rules created by pFSense and define only ports you would like to use – only that way you can block unwanted traffic and better control your LAN-> WAN traffic.
Here is my default configuration for internet access
DNS rule HAS TO BE ALLOWED, and with both TCP/UDP protocol, otherwise your clients won`t be able to access internet.
By this short tutorial you can successfully define rules that will either allow of block some traffic from your network, in this example we covered blocking, but If you want to allow something, procedure is the same, except you’ll choose allow instead of block rule.
pFSense article series:
How to install pFSense on Hyper-V – https://www.informaticar.net/how-to-install-pfsense-on-hyper-v/
How to configure pFSense – https://www.informaticar.net/how-to-configure-pfsense/
How to define firewall rules on pFSense – https://www.informaticar.net/how-to-define-firewall-rules-on-pfsense/
How to create port forwarding on pFSense – https://www.informaticar.net/create-port-forwarding-on-pfsense/
How to setup OpenVPN on pFSense – https://www.informaticar.net/how-to-setup-openvpn-on-pfsense/
How to setup OpenVPN on client (pFSense) – https://www.informaticar.net/how-to-setup-openvpn-pfsense-version-on-client-pc/
OpenVPN on pFSense: Enable access to the LAN resources – https://www.informaticar.net/openvpn-on-pfsense-enable-access-to-the-lan-resources/
How to revocate user certificate on pFSense – https://www.informaticar.net/how-to-revocate-user-certificate-on-pfsense-openvpn/
How to import PFX certificate to pFSense – https://www.informaticar.net/how-to-import-pfx-certificate-to-pfsense/