Support for HTTPS is a must for every website or app created in todays world. In this tutorial we will install mod_ssl module for Apache, enable it and create self-signed certificate for our installation.
Prerequisite for this tutorial is installed and configured Apache webserver.
EDIT: If you don’t have it install yet, you can check out my LAMP installation guide and install it – https://www.informaticar.net/how-to-install-lamp-stack-on-centos-red-hat/
I will run all commands as root user.
Install mod_ssl
Here is simple command for mod_ssl module installation
dnf install mod_ssl
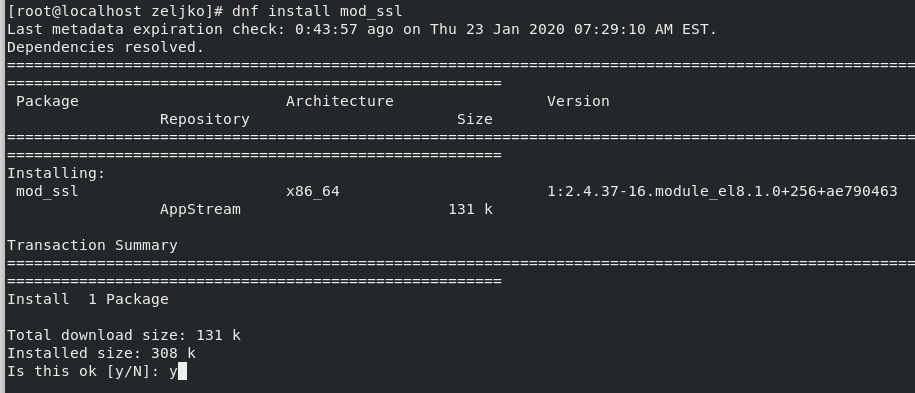
After installation we will restart httpd service so that mod_ssl becomes active.
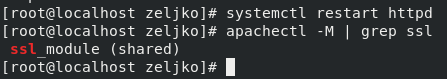
First command will restart web server, and second one will check if the mod_ssl module is active.
systemctl restart httpd
apachectl -M | grep ssl
Everything is ok with my installation.
Last step in mod_ssl installation would be to open HTTPS 443 port through firewall.
firewall-cmd --zone=public --permanent --add-service=https
firewall-cmd --reload
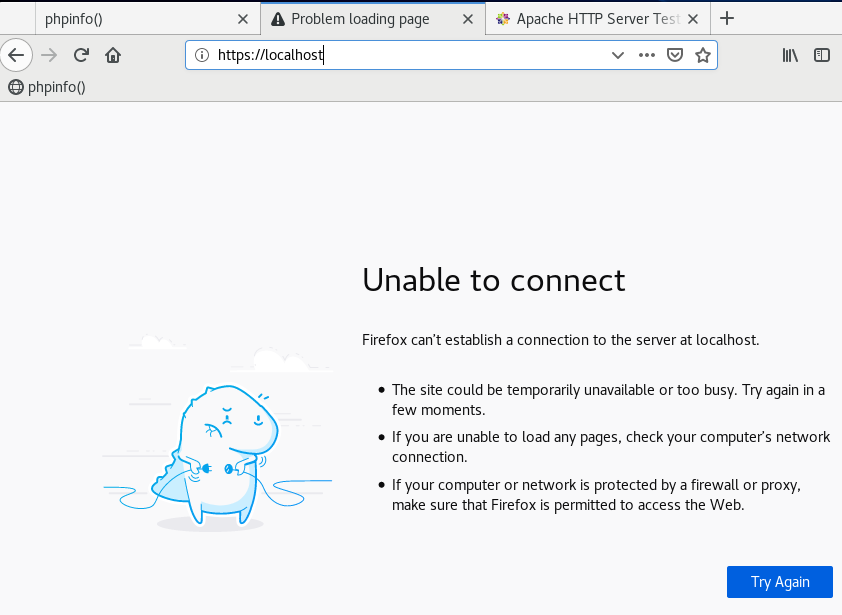
If everything went ok, you should open your web browser on server on which you set Apache and mod_ssl and open https://localhost
Before mod_ssl installation localhost was not accessible via https
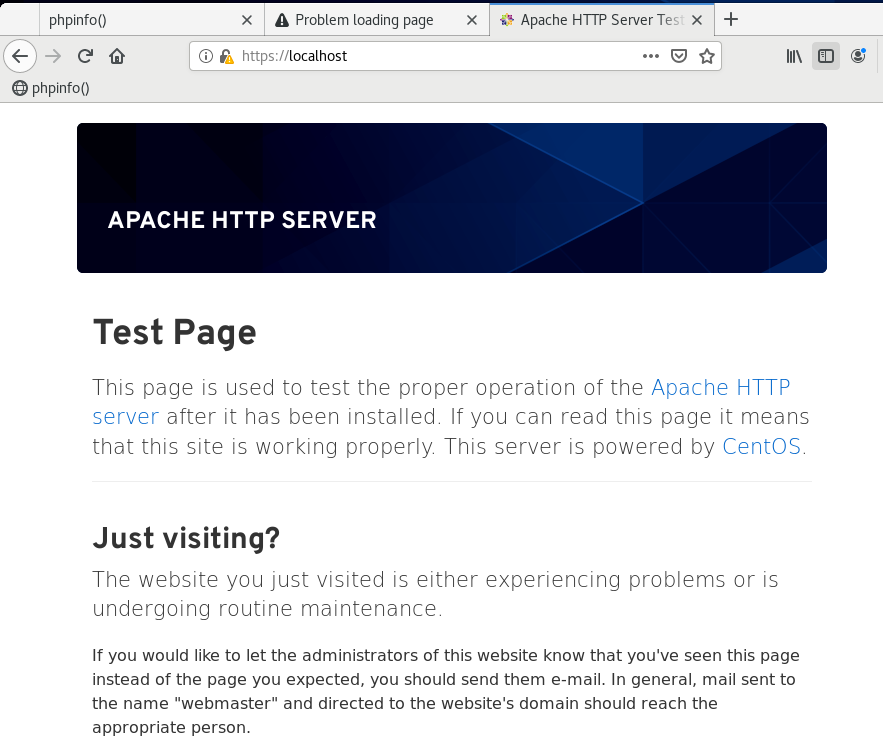
After mod_ssl install our webserver is accessible via https
Generate SSL certificate
In case you do not have proper SSL certificate (which I recommend getting) you can generate your own self signed certificate. It will be good enough for some lab testing.
Ok, we will create certificate which will be valid for 365 days and it will be saved in /etc/pki/tls/certs and /etc/pki/tls/private directory.
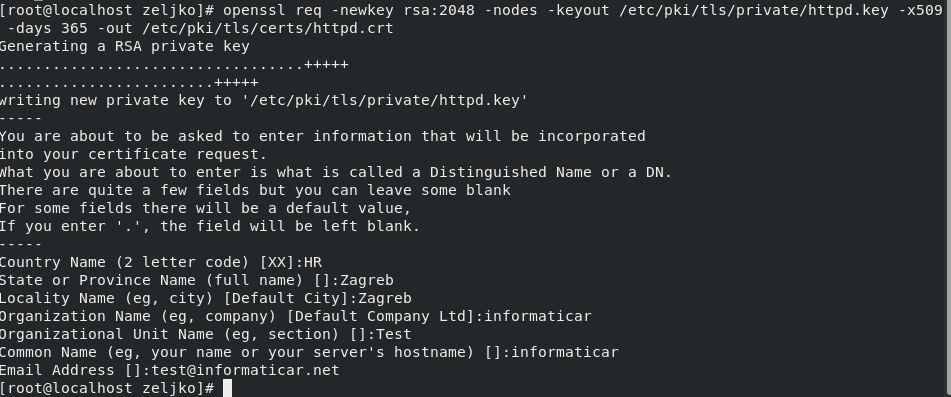
openssl req -newkey rsa:2048 -nodes -keyout /etc/pki/tls/private/httpd.key -x509 -days 365 -out/etc/pki/tls/certs/httpd.crt
You will be asked for some details as if you are buying a real cert
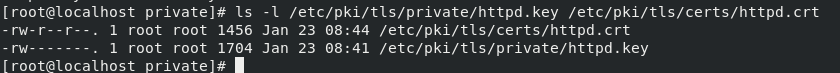
Here are the locations of the created certs
ls -l /etc/pki/tls/private/httpd.key /etc/pki/tls/certs/httpd.crt
Ok, now we need to tell our webserver to use created certificates.
we need to edit file /etc/httpd/conf.d/ssl.conf
vi /etc/httpd/conf.d/ssl.conf
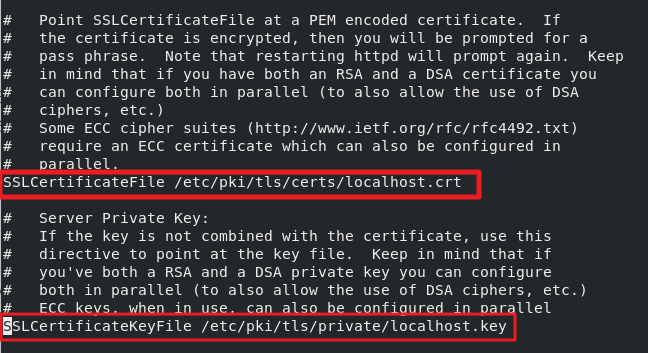
We need to find two values in this file:
SSLCertificateFile /etc/pki/tls/certs/localhost.crt
SSLCertificateKeyFile /etc/pki/tls/private/localhost.key
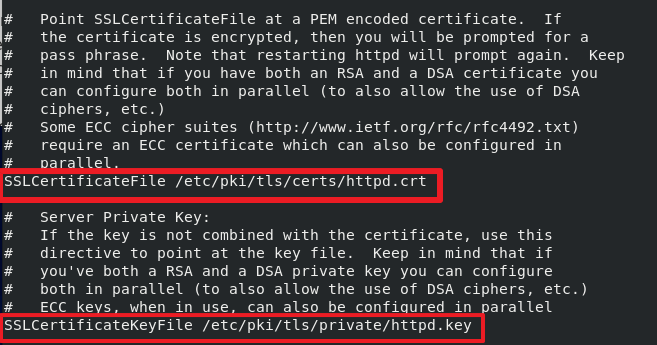
And change them to:
SSLCertificateFile /etc/pki/tls/certs/httpd.crt
SSLCertificateKeyFile /etc/pki/tls/private/httpd.key
Save your changes and exit file
Restart web server
systemctl reload httpd
Back to the browser, enter again https://localhost (you can also enter ip address, or better yet name, depends how you configured your lab.)
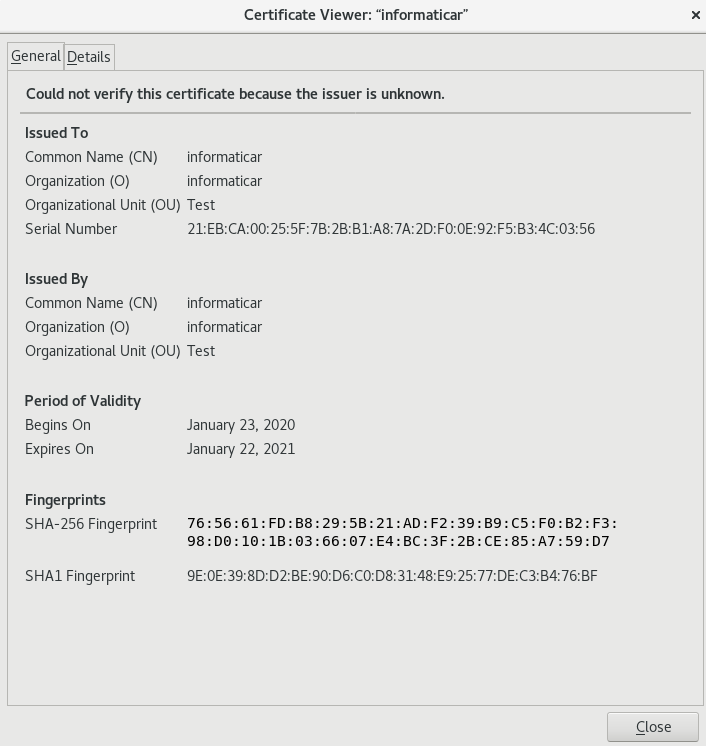
As you can see, I’m using created certificate.
HTTP to HTTPS redirection
As a bonus step we can configure HTTP to HTTPS redirection.
Create redirect_http.conf in /etc/httpd/conf.d/
vi /etc/httpd/conf.d/redirect_http.conf
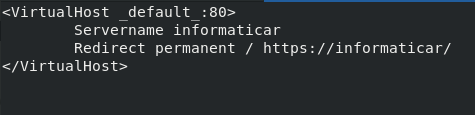
Enter following into file
<VirtualHost _default_:80>
Servername yourservername
Redirect permanent / https://yourservername/
</VirtualHost>
After that you will need to restart httpd
systemctl reload httpd
And that would be it.