I already went through setting up Fortigate on Azure Stack – you can read more about it here https://www.informaticar.net/how-to-install-and-configure-fortigate-vm-on-azure-stack/ but the part that is missing is – how to allow access to VMs behind Fortigate in Azure Stack?
We have to do simple port forwarding.
Prerequisites
This tutorial is done on Azure Stack v 1.1910.0.58
Fortigate VM (from Azure Marketplace) is v 6.0.3
Fortigate network config:
Internal network is on 172.16.2.0/24 (assigned to port2 on Fortigate with IP 172.16.2.4)
Outside network is on 172.16.0.0/24 (assigned to port1 on Fortigate with IP 172.16.0.4)
IP address of the VM I want to access from outside is 172.16.2.5
Public IP that Azure Stack assigned to Fortigate is 192.168.102.34
I want to access VM from outside and I want to access it via RDP.
Configuration
First step would be to define Virtual IP on Fortigate.
Policy & Objects | Virtual IPs | + Create New | Virtual IP
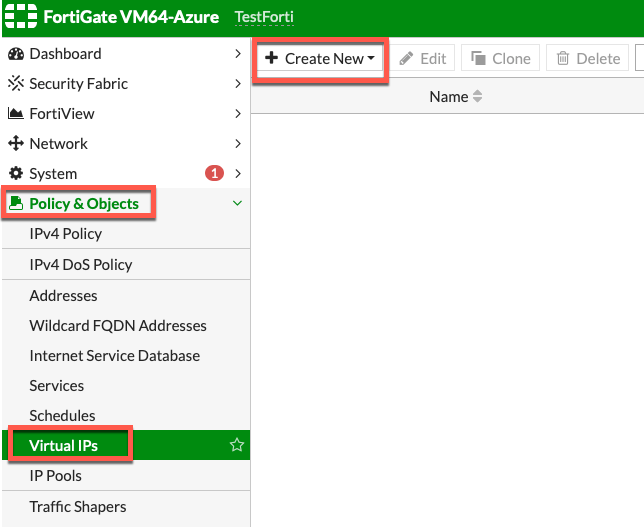
Ok, here is a little explanation of the New Virtual IP screen. Name and Color is up to you, interface should be your Outside interface (WAN), in my case it is port1. External IP Address – it is not public IP Azure assigned to your Fortigate, it is IP address of the Outside interface of your Fortigate installation. It is defined under Network | Interfaces – in my case it is on port1 with IP address 172.16.0.4
Mapped IP is the IP on the internal network you wish to access. My VM is on IP 172.16.2.5. Finally – enable Port Forwarding and define port you wish to forward. I want RDP so for me both external service port and map to port is 3389. OK
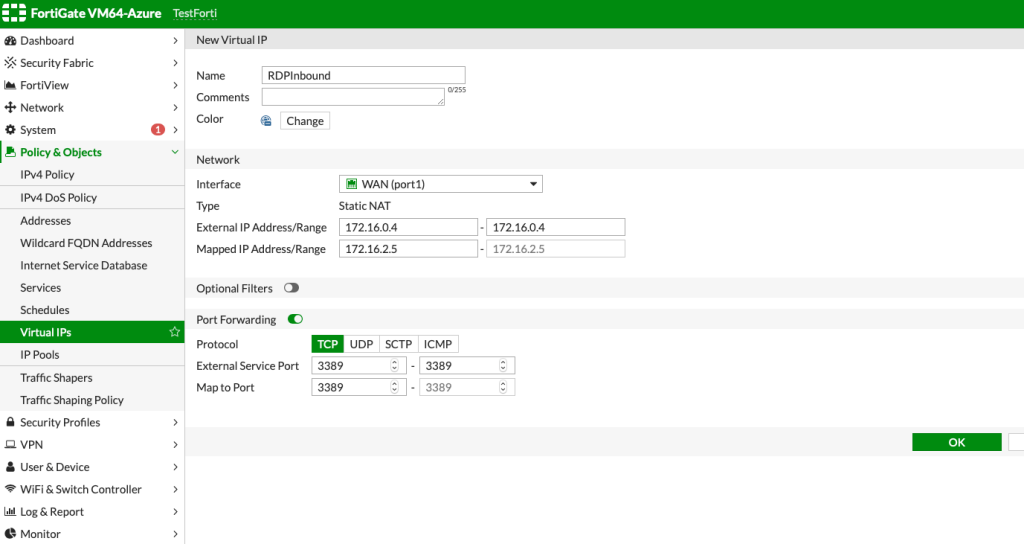
Here is what created Virtual IP looks like.
Next step
Policy & Objects | IPv4 Policy | + Create New
So, here is how my policy looks like. Name – again, up to you. Incoming Interface should be your Outside (WAN) interface – port1 in my case. Outgoing interface shoud be your inside (LAN) interface. Source – we can select all, and Destination, we will select created Virtual IP – in my case it is under RDPInbound name. We wish this rule to be accessible always and service we want to let through is RDP. Action is Accept and NAT is ON!!!
Leave everything else as default or configure to your liking – confirm with OK
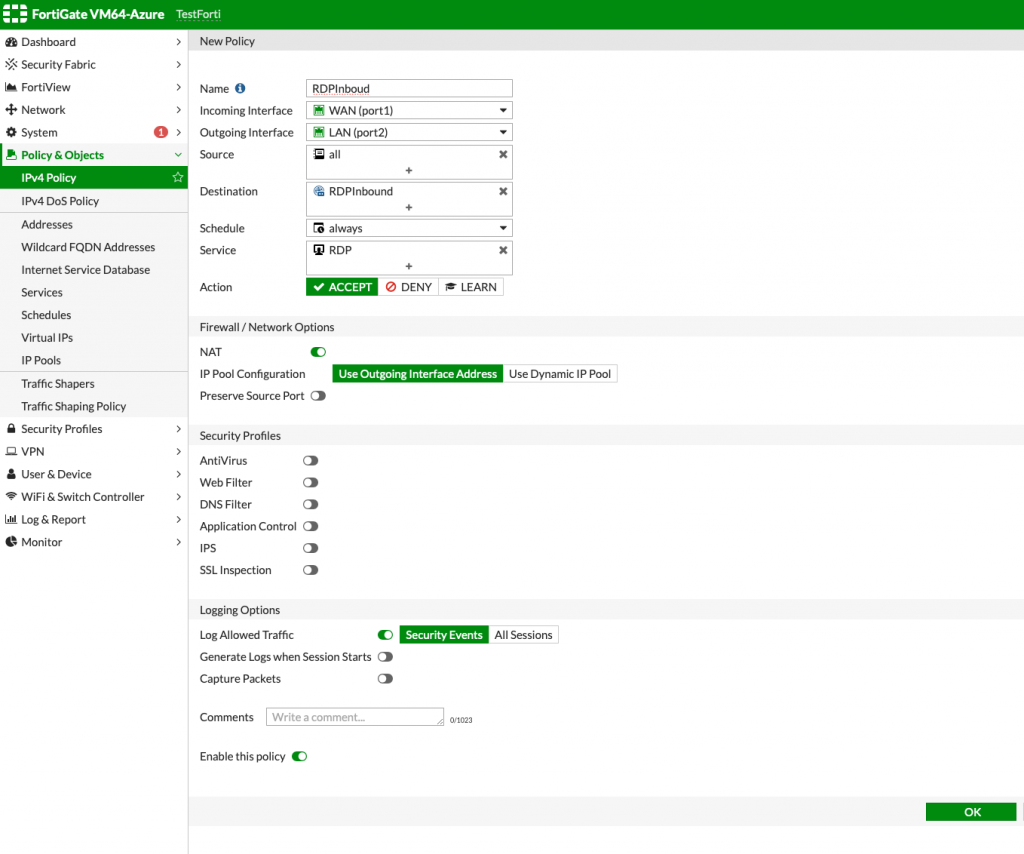
This is how created rule will look like.

Now, to the test. I created RDP connection on my machine with port 3389 and external IP that Azure assigned to my Fortigate installation – 192.168.102.34
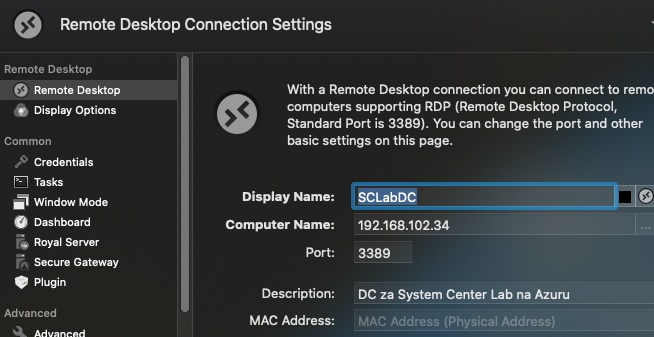
We will now try and connect
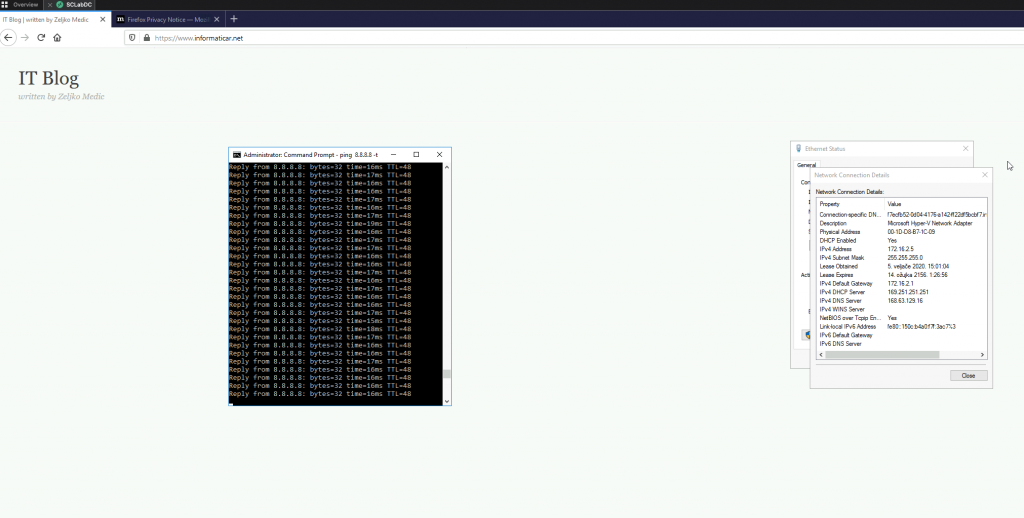
Success! It works.
That is it.
In case this doesn’t work for you, check out once again your Fortigate configuration and Routes part on your Azure Stack.