You want to delegate simple administrative tasks in AD like adding/modifying users, resetting passwords to some of your users or junior IT staff and you are wondering how to do it without granting them Domain Admin rights? Read on, there is an elegant solution to your problem.
I already covered installation of RSAT tools here – https://www.informaticar.net/how-to-administer-active-directory-from-client-pc/
That is a main prerequisite to move on with this tutorial.
Idea is that user can administer AD from it own PC without a need to login to the DC or some other important server in your domain.
After you are done with installing RSAT tools on the client PC read on.
This short tutorial will cover simple administration of AD OU which contains domain user accounts. Tutorial will cover rights to add or remove user accounts on AD for simple user.
In this example Administrator is Domain Admin and Zeljko.Medic is simple domain user with no admin rights anywhere.
Domain Admin will grant user Zeljko.Medic rights to create or delete user accounts in OU named “Korisnici”
On client PC (Windows 10 Pro) from Windows Administrative Tools start Active Directory Users and Computers
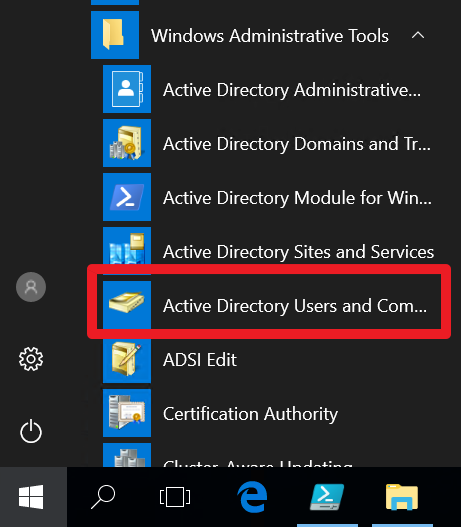
If I try to add new user to the OU “Korisnici” with user Zeljko Medic here is the result:
Access id denied. User Zeljko Medic does not have rights to create objects in AD.
Now, to the AD Server (Windows Server 2012 R2) login with Domain Admin, in my case that is user Administrator.
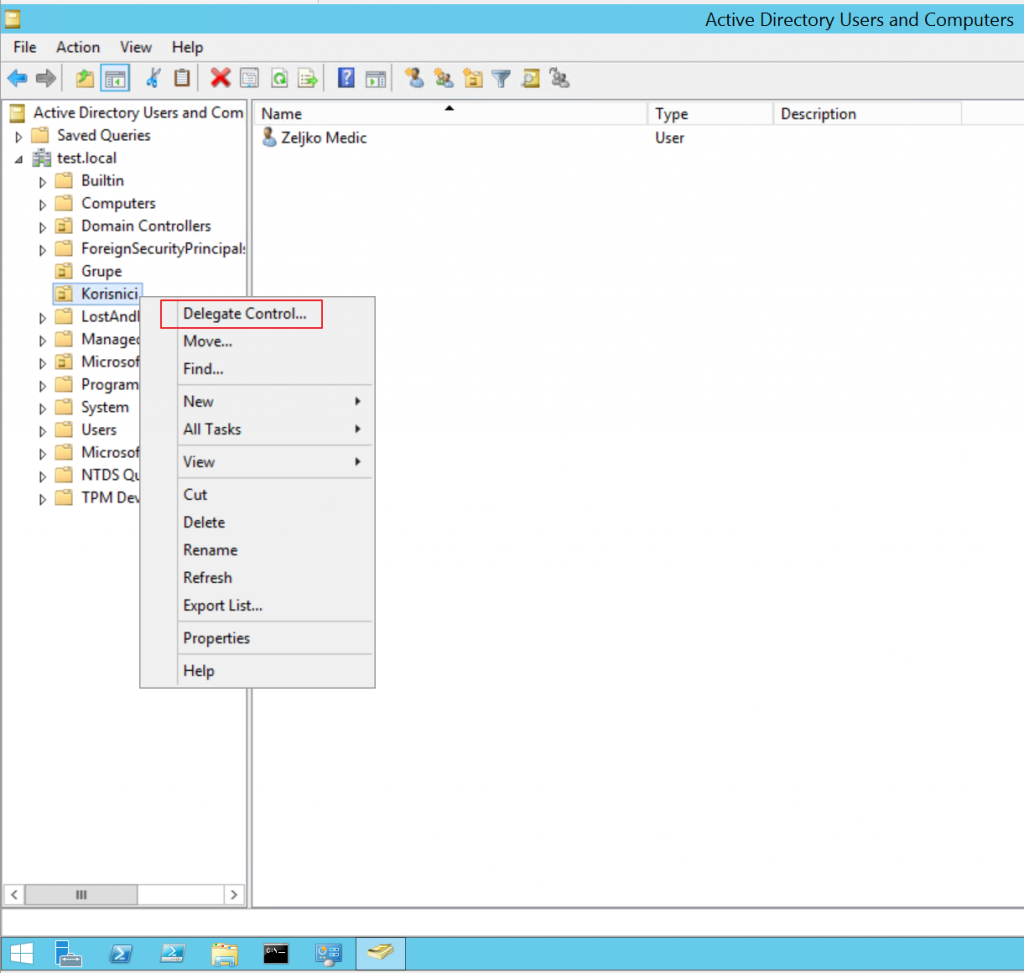
Go to the Active Directory Users and Computers and right click on the OU you wish to grant access to. In this case it will be OU “Korisnici” | Select Delegate Control
Next
On the Users or Groups screen we need to select the user (or group) that we want to delegate rights to. | Click on Add
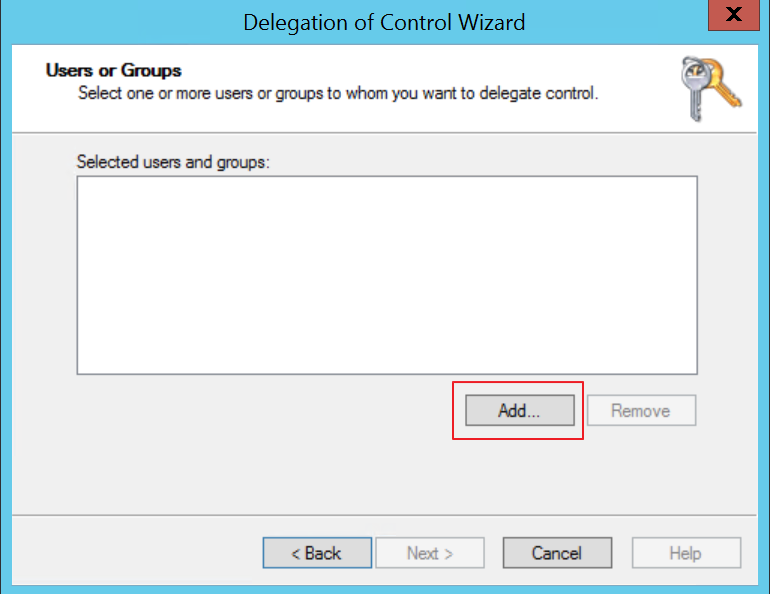
Enter the name of the user or group you wish to delegate righrs to, and click on Check Names. If everything turns up as it should, your entry should be confirmed and you can click on OK
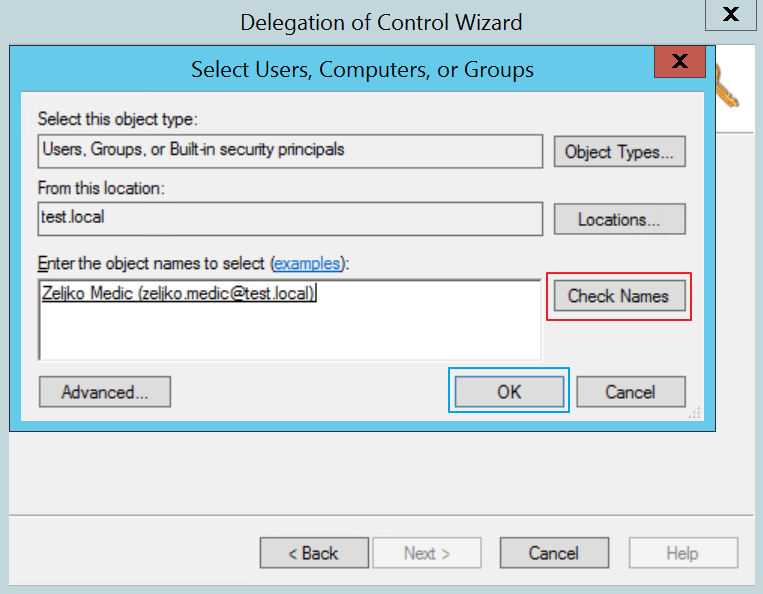
User is entered, click on Next
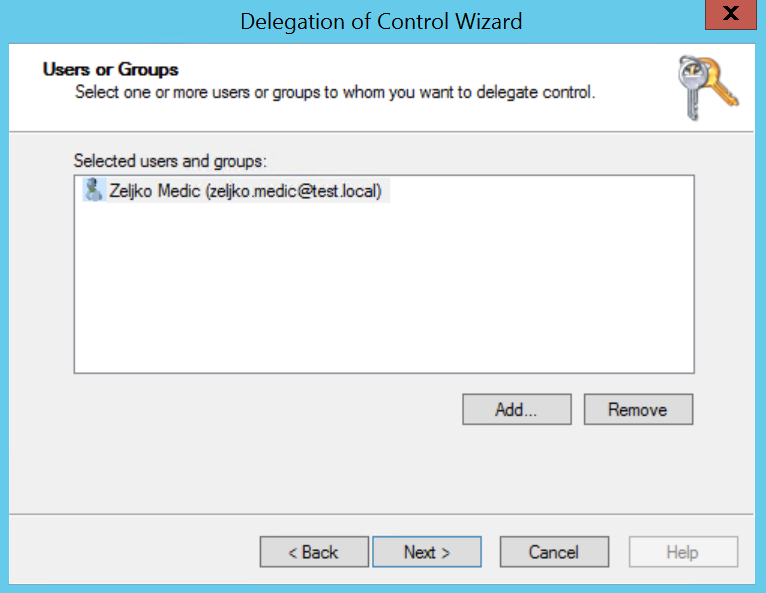
Now, on this screen you should choose the rights you want to delegate to the user. For this tutorial we are going to choose “Create, delete, and manage user accounts” | Next
Finish
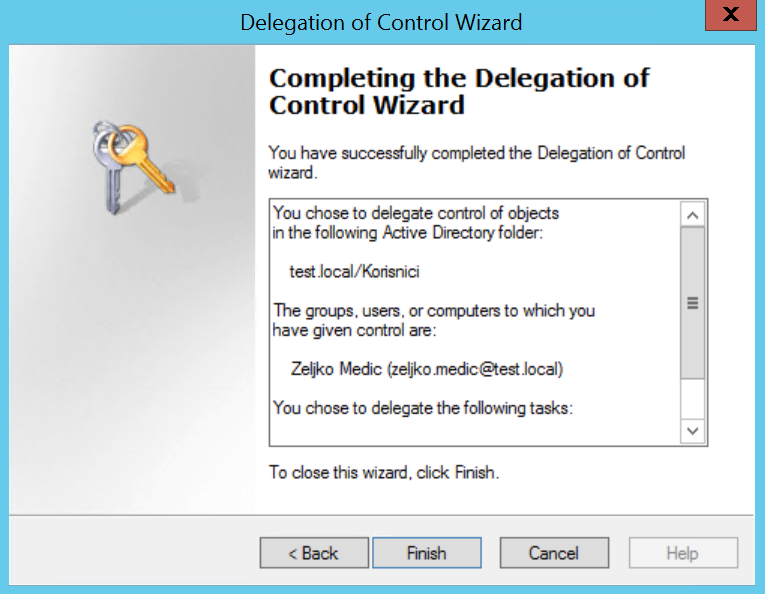
Now, if we did everything right we should now be able to add new user account to the AD from the client PC and user that is logged in as Zeljko Medic (simple user, no admin rights locally or on domain).
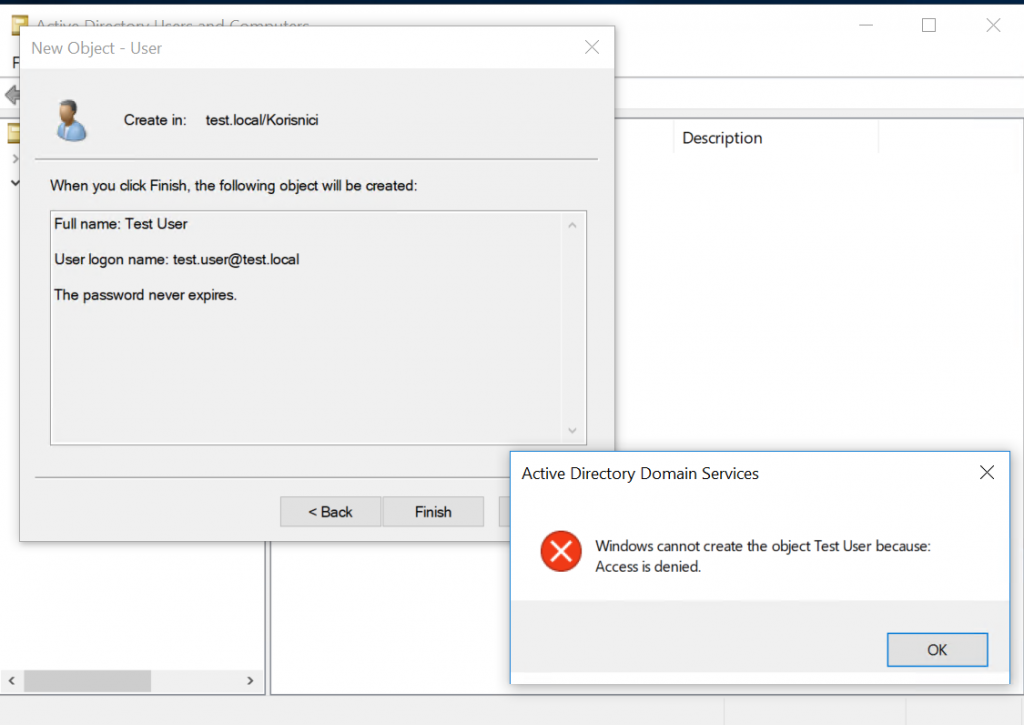
Let us try again by adding user “test.user” to the AD that we were not able to add in the beginning of this article.
I will not describe procedure of creating new user in AD.
This is the last screen of the creation of new user, just before I click on Finish
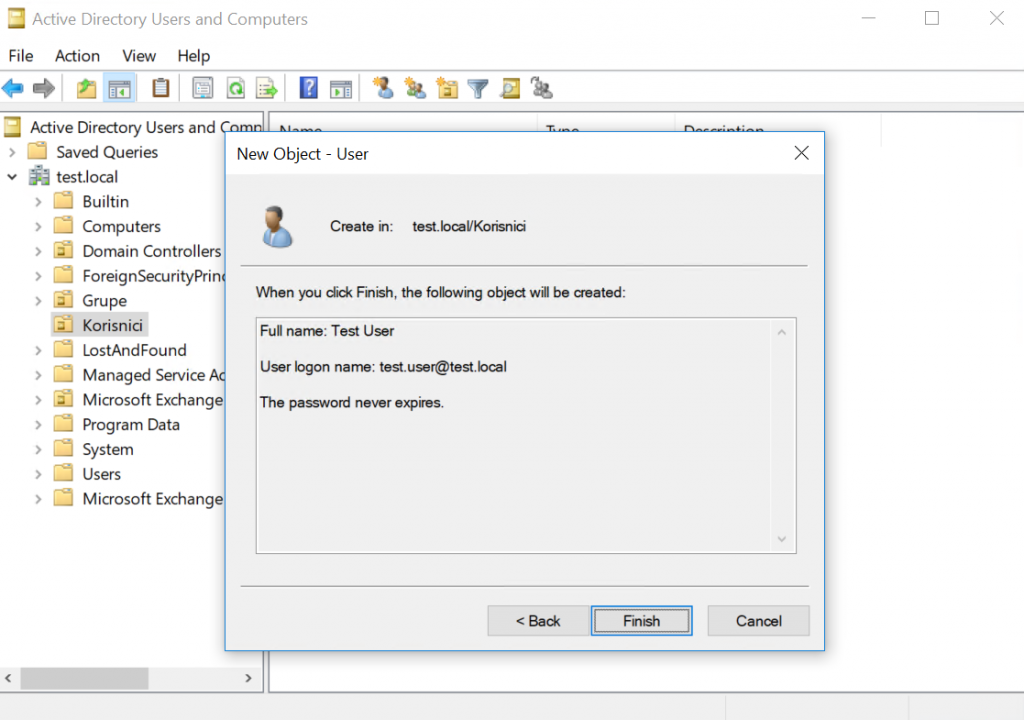
Moment of truth..
New user is created!!
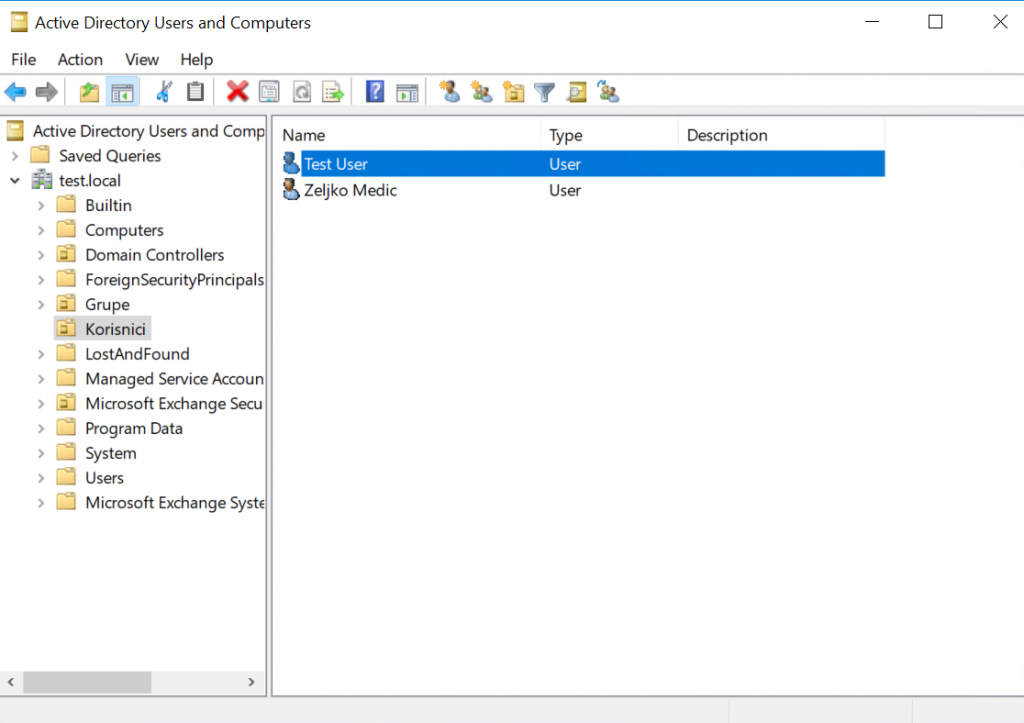
That is it and this way you can delegate simple/repetitive administrative tasks on the AD to domain users without having to fear they will bring down whole network.
This procedure is also valid if you wish to assign rights to the group of users rather than a single user (groups are always more elegant solution).
Also if you have powershell scripts in place for administrative tasks they also should work from the user account you assigned them to.